By now, you likely know the basics of FedRAMP, especially if you’ve read our robust coverage of the program. But, like all good cybersecurity frameworks, it evolves and changes over time, and our knowledge needs to be updated.
One recent development is the 20x pilot program, which entered phase one in March of 2025. What is this pilot program, what does it do, and who is it for? Read on to learn more about 20xP1 and what it means for you.
 BLUF - Bottom Line Up Front
BLUF - Bottom Line Up Front
The FedRAMP 20x pilot program offers a faster path to authorization for cloud providers looking for Low Baseline impact level. It replaces some traditional security controls with Key Security Indicators (KSIs) to increase efficiency. The program boosts automation, reduces continuous monitoring, and facilitates faster authorization within three months. Companies can apply by reviewing KSIs, preparing reports, and coordinating with a certified assessor. Its insights may aid future updates to the Moderate authorization process.
What is the FedRAMP 20x Pilot Program?
It’s no secret that achieving a full FedRAMP authority to operate is a lengthy, time-consuming, and very detailed process. Even the low impact level, with the fewest security controls, can take 12-18 months of dedicated work before a cloud service provider achieves their goals.
This significant barrier is proving to be a roadblock to both businesses and the government, so the government has been taking steps to try to improve the process, either by streamlining the overall authorization process, adjusting security controls and the language around them to be easier to understand, or rolling parts of the program together to reduce confusion.
Another element of this goal to streamline and modernize FedRAMP is the 20x Pilot.
The goal of the pilot program is two-fold.
First, it aims to provide a faster, streamlined process for FedRAMP authorization. In the case of the phase one pilot program, this is aimed specifically at cloud service providers looking to achieve the FedRAMP Low Baseline impact level.
Second, it serves as an experiment in modernizing the FedRAMP process through the use of automation, a change to documentation and proof, and the removal of friction and roadblocks to authorization. This allows the GSA to see what works and what doesn’t, so another iteration on the pilot program can further modernize the process.
The government gets a more streamlined process, and a bunch of low-level cloud service providers get a faster process to reach a 12-month Low ATO with priority for increasing their authorization to Moderate in later phases of the program.
Introducing KSIs
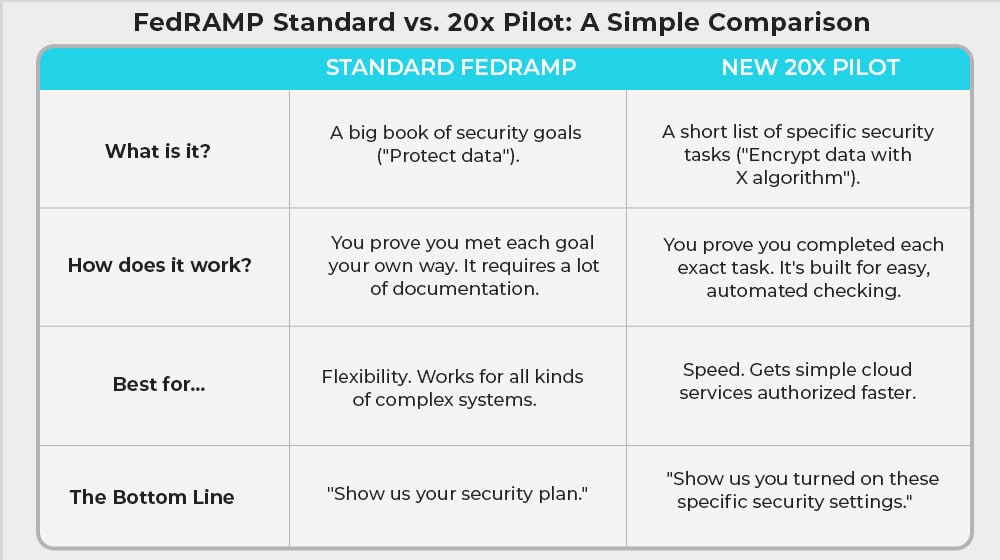
One of the main differences between the standard FedRAMP low baseline authorization process and the new 20x pilot program is a change in what the cloud service provider has to do.
FedRAMP relies on NIST SP 800-53, the traditional list of security controls and implementation guidelines that all FedRAMP impact levels draw from. The primary difference between impact levels is the number of controls a CSP has to implement and verify.
Part of the problem with this framework is that, no matter how the controls are revised and optimized, they necessarily need to be broad and flexible. Too many companies across too many different industries and frames of functionality need to adhere to them. The more specific and narrow they are, the more problems can crop up with companies outside of the narrowly defined range.
The 20x pilot program serves to, in a sense, replace NIST SP 800-53 for the purposes of low baseline authorization to operate. It does so by using KSIs, or Key Security Indicators, instead.
KSIs are specific and measurable tasks and outcomes, rather than broader or more generalized security controls. In a sense, it’s less of a list of goals and more of a list of tasks.
KSIs are still related to security controls. Many KSIs have “related controls” that they reference, for organizations that want more background information on how to implement them.
Additionally, a whole list of security controls is omitted from KSIs. While these controls can still be important, they aren’t required for authorization along the 20x program. The omitted controls, specifically, are:
- Access Control AC-8, AC-18, and AC-19
- Awareness and Training AT-1, AT2-(2), and AT-4
- Audit and Accountability AU-5 and AU-6
- Security Assessment and Authorization CA-2, CA-2(1), CA-5, CA-6, CA-7, CA-7(4), and CA-8
- Configuration Management CM-5
- Contingency Planning CP-3
- Incident Response IR-2
- Planning PL-4, PL-4(1), PL-8, PL-10, and PL-11
- Personnel Security PS-6
- Risk Assessment RA-2
- System and Services Acquisition SA-4(10)
- System and Communications Protection SC-15, SC-20, SC-21, and SC-22
- System and Information Integrity SI-12
- Supply Chain Risk Management SR-11(1)
Additionally, all controls under Maintenance, Media Protection, and Physical and Environmental Protection are excluded.
This cuts down on the work significantly. Many of these controls are specifically related to personnel and administration tasks, which are harder to automate and review; the remaining controls are generally those that can be more easily automated, from implementation to validation to monitoring.
Speeding Up Authorization
Streamlining what needs to be implemented, allowing more automation, and reducing oversight all serve to speed up the process of authorization through the 20x pilot program.
The 20x authorization process looks like this:
- Initial Submission. Your company submits a package that meets the submission requirements, including a C3PAO assessment.
- Initial Review. The FedRAMP organization reviews your submission and reaches out with any next steps or feedback.
- Collaborative Review. FedRAMP will host a discussion with you and your C3PAO to dig into your package, discuss details, identify your overall approach, and give feedback on your process.
- Granting In Process Status. Barring significant problems, you’re granted In Process as a listing on the marketplace. You can now work on any POA&Ms necessary from the review phase.
- Final Submission. Once your task list is complete, you submit a final package mapped to KSIs for final review.
- Comprehensive Review. FedRAMP once again reviews and discusses your package and performs some testing and exercises to validate your status.
- Authorization. Once again, barring significant problems, you are granted full 20x Low Authorization in the marketplace for a period of 12 months.
- Monitoring. As always, continuous monitoring and regular reporting are required to maintain your status.
While a lot of work is summarized in that first step, as you can see from the list of omitted security controls above, it’s a lot less work than it was in the standard process.
Speaking of monitoring, another big change from FedRAMP Low to 20xP1 is a reduction in continuous monitoring. In particular, in addition to no longer needing to monitor controls you don’t need to implement, some KSIs have changed from continuous monitoring to monthly status reports, further alleviating the ongoing burden of maintaining authorization.
The Benefits of 20xP1
What are the tangible benefits of participating in the 20x program pilot?
The pilot offers a faster and more streamlined process.
The biggest benefit is a faster turnaround time for authorization. Even under the traditional FedRAMP Low Baseline process, authorization could take 12-18 months, and that’s when everything is going smoothly and there are relatively few issues to address along the way.
In comparison, as of the three-month mark of the 20xP1 pilot program, seven companies have full FedRAMP authorization, and another two are in process. Full authorization in three months instead of 18! Moreover, four CSPs had authorization within the first month. Last year, that would have been unheard of.
The pilot allows automation that isn’t accepted under the normal process.
A huge part of why the entire process is faster and more streamlined is that a lot of it can be done with automation. Validated automation platforms allow for machine-readable implementation and reporting, which eliminates a huge amount of time-consuming work. While the pilot program is still new and the available automation programs are limited, it’s still much, much better than it was before.
To facilitate this automation, FedRAMP has published both a public roadmap and a tangible task list on GitHub. This wasn’t published to much fanfare, but is already proving to be an invaluable resource.
The pilot encourages transparency to help others follow suit.
Several companies that have achieved authorization through the 20x pilot program have published their submissions publicly with the encouragement of the FedRAMP program management office. This allows other cloud service providers to see how it’s all done.
On this page, FedRAMP links to the submissions for InfusionPoints, Vanta, Flock Safety, and Knox, as examples of how submissions can be handled.
The pilot promises a fast-track process to moderate authorization.
There’s a significant hurdle here. Low baseline is fine for a lot of cloud native CSPs that handle essentially no CUI outside of login information, similar to the Li-SaaS baseline level. However, for companies that would need a higher level of authorization, this isn’t secure enough for operations.
Since over 80% of CSPs end up in the Moderate baseline level, the vast majority of CSPs can’t use the 20x pilot program for their authorization. Or can they?
One part of the goal of the pilot program is to see how well streamlining the authorization process can work, and to lay the groundwork for similar changes at the moderate (and, eventually, high) baseline levels. CSPs that are able to restrict the information they use to what can be secured under 20x Low can achieve authorization via the pilot program, and be added to a list of priority authorizations for the next phase of the pilot program, where moderate is supported.
It remains to be seen how this will work – it’s still over half a year out – but it’s one significant potential benefit.
How to Join the 20x Pilot Program
If you’re interested in taking part in this streamlined authorization process, it’s still available. The steps you should take depend on where you were in the process already.
If you’re already in the process of working for the standard authorization process, you should stay working on it as you have been. While it can be tempting to drop everything for the promise of a sub-three-month authorization, it can cause confusion and conflicts, and there’s still a lot of work and adjustment to be done in the switch from NIST SP 800-53 controls to KSIs.
If you’ve been doing the work and were about to apply for the FedRAMP authorization process, you have a choice to make. A full or near-full implementation of Low Baseline security controls is likely to be higher than KSIs, but switching to KSIs will still take work to adapt what you’ve been doing. Many organizations will find sticking with the legacy program will be better, unless it’s very easy to make the shift.
If you have no real way to isolate your systems down to a low baseline equivalent, you’ll need to stick with the current Moderate authorization process. That said, if you aren’t heavily reliant on an impending contract, you might wait until the end of 2025, when the goal is to start the 20x phase two for moderate authorizations.
If you’re ready and able to apply for the pilot program, here’s what to do.
- Lay the groundwork. Review the KSIs list (using whichever version is newest, currently the May Formal document) and implement them, develop your report package, and work with a C3PAO for an initial assessment. Compile all of this into your initial package.
- Email 20x@fedramp.gov. Your email should include a summary of your CSP and service offering, your points of contact for yourself and your C3PAO, and instructions on how to access your initial package. DO NOT email the initial package directly.
- Wait for further instructions.
Your initial package needs to include a lot of information that FedRAMP will review. This isn’t your typical evidence package, either. You need a summary and a rationale for the approach you used to generate your submission, such as which tools you use to automate and why. You’ll need validation of this approach from your C3PAO, as well.
Additionally, the standard evidence applies. KSI listing with validation status, evidence and links, underlying information, and integrated C3PAO verification, in both human-readable and machine-readable formats, make up the bulk of the package. You’ll also need a data definition or schema for explaining the machine-readable half.
As a FedRAMP C3PAO, we can help with a significant part of this, so feel free to reach out and see what we at Ignyte can do for you.
Max Aulakh is a distinguished Data Security and Compliance leader, recognized for implementing DoD-tested security strategies and compliance measures that protect mission-critical IT operations. His expertise was shaped in the United States Air Force, where he was responsible for the InfoSec and ComSec of network hardware, software, and IT infrastructure across global classified and unclassified networks. He also developed strategic relationships with military units in Turkey, Afghanistan, and Iraq. After his tenure with the USAF, Max played a pivotal role in driving Information Assurance (IA) programs for the U.S. Department of Defense (DoD). As a Senior Consultant for a leading defense contracting firm, he led a team that ensured data centers met Air Force Level Security audits for regulatory requirements like HIPAA, SOX, and FISMA. Currently, as the CEO of Ignyte Assurance Platform, he is at the forefront of cyber assurance and regulatory compliance innovation, catering to defense, healthcare, and manufacturing sectors. Max is also an esteemed speaker, having presented at several conferences on topics including cybersecurity GRC, medical device security, and cybersecurity perspectives in vendor management. You can follow him in LinkedIn here.



 BLUF - Bottom Line Up Front
BLUF - Bottom Line Up Front