Navigating the federal government’s cybersecurity standards and processes is not easy. Figuring out how to comply with all of the various standards and controls is a lengthy process involving thorough auditing and analysis of your entire organization from top to bottom.
When government contracts and sensitive information is at stake, though, it’s all taken very seriously. Today, we’ll talk about the FedRAMP impact levels and explain each one.
 BLUF - Bottom Line Up Front
BLUF - Bottom Line Up Front
Navigating federal cybersecurity standards is complex but crucial for government contracts. FedRAMP impact levels classify cloud services into Low, Moderate, and High, based on potential risks if data is compromised. Low impact involves basic public information, Moderate handles sensitive but unclassified data, and High impact deals with critical operations, possibly affecting national security. Providers must assess their systems, aim to adhere to required security controls, and possibly modify operations to meet lower impact levels.
Not All Cloud Providers Are Created Alike
One of the realities of this world we live in is that not all companies, not all services, and not all information is created alike. Some things are simply more important than others.
FedRAMP acknowledges this with the use of impact levels. When a cloud service provider is bidding on a contract with the federal government in one of its many agencies, that cloud service provider must adhere to certain baseline standards of cybersecurity. These baselines are defined through the Federal Information Processing Standard 199, or FIPS 199. You can see the full text of FIPS 199 here.
There are three levels of impact defined in FIPS: Low, Moderate, and High. We’ll dig deeper into defining these in a moment, but a simple way to think of them is in terms of personal impact.
Imagine, for a moment, that a database somewhere is hacked, and that database contains information about you. How much should you be concerned, and how much damage could be done to your life? It depends on the kind of information that is compromised.
- The low impact level would be the equivalent of a database that contains your name, phone number, email address, and other publicly available information. You might end up with more robocalls or spam emails, but there’s very little that a malicious actor could do with that information, all of which is available publicly through various other channels.
- The moderate impact level would be the equivalent of a database that contains your account passwords, bank information, and other personally identifiable information. This is information that can be used to steal your identity, drain your bank account, and cause other problems. The impact is a huge hassle, but there are generally mechanisms in place to remediate the damage, such as freezing your credit and taking advantage of bank insurance to roll back fraudulent transactions.
- The high impact level would be the equivalent of the malicious actor being able to access things like your passport, your social security number, and your multi-factor authentication services. With it, not only can they steal your identity, they can cascade that compromise into other compromises, in a devastating web of consequences.
Expanding this to the federal government, you can see why the division would be significant. Low impact is significant but doesn’t necessarily impact daily operations more than the agency requiring additional phishing awareness training. The moderate impact level has a significant impact on operations, but doesn’t necessarily hinder the government or the country as a whole. The high impact level, meanwhile, can have devastating consequences for the nation.
It’s no wonder, then, that cloud service providers should be held to higher standards when their impact is higher. A service that does nothing more than maintain contact information and address books for agency employees is very different than the platform that administrates critical agency operations.
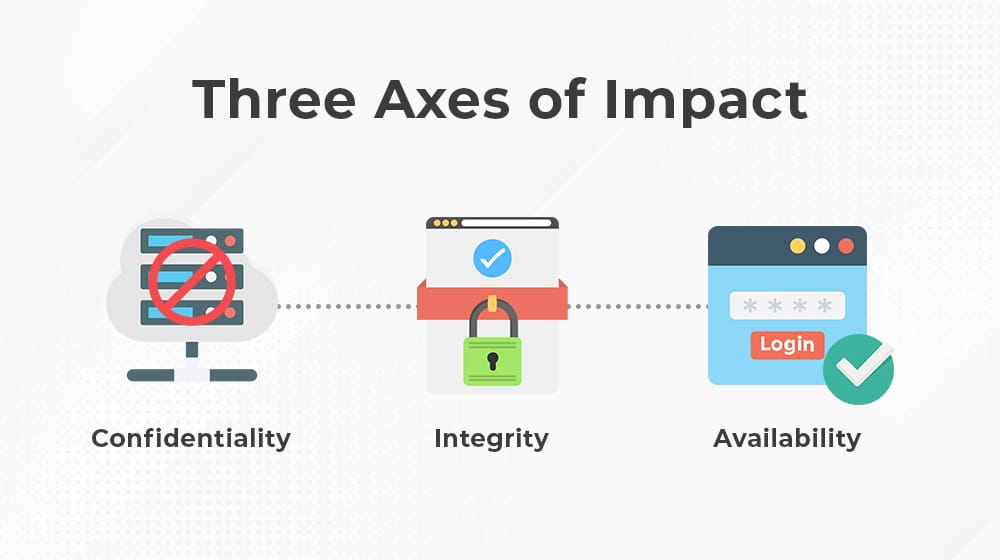
Three Axes of Impact
Every cloud service provider that intends to achieve FedRAMP certification needs to analyze their services across three axes. Each of the three has its own impact level, for a total of nine possibilities. Generally, though, FedRAMP does not allow for customization between these; the highest impact level on any of the three axes is the impact level the cloud provider must adhere to.
The three axes are:
- This is about preserving restrictions on sensitive information access and disclosure, along with maintaining a means for the protection of personal and proprietary information and privacy.
- This is about maintaining the information within the system, and protecting it against unauthorized access, destruction, or modification. It also includes means for verifying the authenticity of information within the system.
- This is about ensuring reasonable access to and use of information within the system.
Availability may seem like the odd one out, but it’s more important than it might seem at first glance. After all, if you file away all information in a black box that can never be opened, it’s certainly confidential and secure against unauthorized access, but it does no one any good when they need to make use of that information. Availability ensures that access to the information is reasonable and timely, while still ensuring that only authorized personnel are able to access it in the first place.
So, again, the information the cloud service provider accesses, stores, and uses in their operations will determine the impact level required for each of these three axes, and the highest impact level for any of the three sets the minimum for all three.
Low Potential Impact
Low impact cloud services are those that work with the federal government and handle information that is generally publicly available.
If the loss of confidentiality, integrity, or availability of that information were to happen, it would have little or no real impact on the operations, assets, or individuals of the agency in question.
- Confidentiality: The unauthorized disclosure of information could be expected to have a limited adverse effect on organizational operations, organizational assets, or individuals.
- Integrity: The unauthorized modification or destruction of information could be expected to have a limited adverse effect on organizational operations, organizational assets, or individuals.
- Availability: The disruption of access to or use of information or an information system could be expected to have a limited adverse effect on organizational operations, organizational assets, or individuals.
Low-impact businesses don’t deal with personally identifiable information beyond the very basics required for authentication, like a username, password, and email address. There may be some information beyond that stored or used within the system, but in general it’s very little, and the impact if the system is compromised is very minor.
Lower Than Low Impact: Li-SaaS
It’s worth mentioning here that the government acknowledges that there are times when a system they use is even lower impact than low impact, and that to hold the cloud provider to rigorous standards is largely a waste of time, effort, auditing manpower, and energy. Thus, they created the Li-SaaS baseline as a secondary baseline for certain cloud providers.
Li-SaaS stands for Low Impact Software as a Service. It’s a control set that was developed for systems that do not store personally identifiable information other than that which is required for login authentication, and nothing else at all. Since there is very little that the SaaS provider handles, a compromise of the system would have very minimal impact; moreover, many of the security controls required for FedRAMP authorization are either inapplicable or streamlined.
Therefore, Li-SaaS existed as a Tailored Authorization option for those specific kinds of cloud service providers. It primarily allows for two things. The first is a streamlined and faster authorization for a low baseline. The second is that agencies can independently validate a selection of the most important security controls for these organizations, rather than a comprehensive and rigorous audit of every control, as in the other impact levels.
Moderate Potential Impact
Moderate impact cloud services are those that work with the federal government and handle information that may not be publicly available. This information may be somewhat sensitive but is generally not classified information.
The loss or disruption of that information would have a more significant impact on the organization and the people in it.
- Confidentiality: The unauthorized disclosure of information could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals.
- Integrity: The unauthorized modification or destruction of information could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals.
- Availability: The disruption of access to or use of information or an information system could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals.
Moderate impact is by far the most common category, because it’s very broad. It encompasses everything from cloud providers that access a small amount of critical data, all the way up to services that manage and store vast amounts of important data. Nearly 80% of all cloud service providers that receive FedRAMP authorization do so at the moderate level. Compromise of this information can even lead to injury to personnel, though it does not lead to loss of life.
Unlike low impact, there is no streamlined secondary standard for use here. FedRAMP certification for moderate and high impact are both full audits and adherence to all security controls, at the stated impact level.
High Potential Impact
High impact services are those that are much more critical to operations and existence as a whole. They can include data involved in realms such as law enforcement, emergency services, financial systems, healthcare systems, and other highly important systems tied to the government.
These are the kinds of systems where disruption of operations can lead to far-reaching consequences for the agency, for the state or nation, for the economy, and to individuals, up to and including potential loss of life. Critical infrastructure and national security fall into high impact.
- Confidentiality: The unauthorized disclosure of information could be expected to have a severe or catastrophic adverse effect on organizational operations, organizational assets, or individuals.
- Integrity: The unauthorized modification or destruction of information could be expected to have a severe or catastrophic adverse effect on organizational operations, organizational assets, or individuals.
- Availability: The disruption of access to or use of information or an information system could be expected to have a severe or catastrophic adverse effect on organizational operations, organizational assets, or individuals.
High impact is not a common category, but it encompasses a wide range of information, with everything from controlled unclassified information that can have a severe impact, all the way up to the most sensitive information the agency controls.
In fact, one of the main reasons why this category doesn’t encompass a larger selection of services used by the government is simply because, once you reach a certain level of impact for the information, the government would rather engineer their own secure system than rely on third-party services. This is why the highest impact information generally found on a FedRAMP-certified cloud provider is CUI, or controlled unclassified information; anything truly classified is much further restricted requirement Secret or Top-Secret Clearance of team members and services they are using.
How to Determine Your Impact Level for FedRAMP Certification Purposes
As a cloud services provider looking to obtain FedRAMP certification to work with the government and its agencies, you need to understand your systems, your purpose with the government, and the information you would be handling. This helps you determine your impact level and, thus, what level of security controls you need to have implemented.
It also gives you the opportunity to potentially re-engineer certain services to store and handle less information (the minimum necessary to perform your duties) and potentially drop your service from high to moderate or from moderate to low impact.
So, how do you determine the impact level of the information and systems within your cloud service?
The first option is to comb through the relevant publications. FIPS 199 and the supplemental publication, NIST SP 800-60 (Guide for Mapping Types of Information and Information Systems to Security Categories) are both relevant.
Of course, with hundreds of pages of government standards and definitions, most of which don’t apply to you, these publications are the slow and tedious way to do it.
A better option is to work with a platform like ours. At Ignyte, we’ve developed a comprehensive system to help any cloud service provider looking to obtain security certification to work with the government. Whether you’re aiming for FedRAMP, NIST SP 800-171, CMMC, HIPAA, ISO 27001 or another framework, we cover them all. We can help you categorize your systems, determine the security controls necessary, figure out your impact level, cut down redundancy and much more.
If you’re interested in seeing what our platform can do for you, feel free to reach out and request a demo today. Alternatively, simply contact us to learn more about what we offer and what we can do for you.
Max Aulakh is a distinguished Data Security and Compliance leader, recognized for implementing DoD-tested security strategies and compliance measures that protect mission-critical IT operations. His expertise was shaped in the United States Air Force, where he was responsible for the InfoSec and ComSec of network hardware, software, and IT infrastructure across global classified and unclassified networks. He also developed strategic relationships with military units in Turkey, Afghanistan, and Iraq. After his tenure with the USAF, Max played a pivotal role in driving Information Assurance (IA) programs for the U.S. Department of Defense (DoD). As a Senior Consultant for a leading defense contracting firm, he led a team that ensured data centers met Air Force Level Security audits for regulatory requirements like HIPAA, SOX, and FISMA. Currently, as the CEO of Ignyte Assurance Platform, he is at the forefront of cyber assurance and regulatory compliance innovation, catering to defense, healthcare, and manufacturing sectors. Max is also an esteemed speaker, having presented at several conferences on topics including cybersecurity GRC, medical device security, and cybersecurity perspectives in vendor management. You can follow him in LinkedIn here.



 BLUF - Bottom Line Up Front
BLUF - Bottom Line Up Front