FedRAMP JAB ATO, P-ATO, and Certification can be a tricky set of requirements to navigate, and the confusion starts early. For example, what are any of those terms, and what do they mean? While some of you already know, everyone has to learn somewhere, so let’s go through and define them, what they mean, and what you need to do to adhere to them.
Beyond that, we’ll help you navigate the process and find the best way to get the accreditation status you need.
 BLUF - Bottom Line Up Front
BLUF - Bottom Line Up Front
FedRAMP ensures secure cloud services for federal government use. Providers must meet standards set by FedRAMP, governed by FISMA and detailed by NIST 800-53. Obtaining Authority to Operate (ATO) and Provisional ATO (P-ATO) involves significant security assessments. A qualified 3PAO conducts audits to verify compliance. ATOs and P-ATOs require ongoing monitoring. Ignyte helps streamline these processes, offering services as a qualified 3PAO and assisting CSPs in navigating FedRAMP complexities.
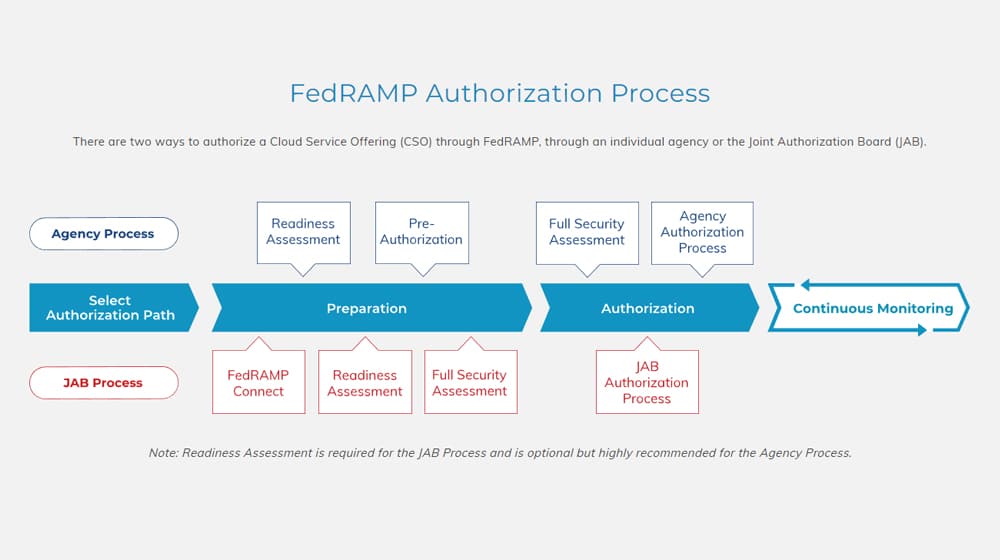
What is FedRAMP and What Does it Do?
Let’s start at the ground level: what is FedRAMP, and what does it do?
FedRAMP stands for Federal Risk and Authorization Management Program. It is:
“…a government-wide program that promotes the adoption of secure cloud services across the federal government by providing a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services. FedRAMP empowers agencies to use modern cloud technologies, with an emphasis on security and protection of federal information.” – FedRAMP.gov.
FedRAMP is essentially a combination of ongoing cybersecurity standards and the process of auditing and ensuring the validity of those security procedures.
The idea goes like this. The government needs to use modern technology to keep up with the world. However, they don’t need to reinvent the wheel. There are many cloud-based services, platforms, and infrastructure operations (collectively, IaaS, SaaS, and PaaS companies) that provide these kinds of operations. The government can use these businesses for their needs.
However, government information, infrastructure, and data must be secure. There are countless threats that would love to compromise a platform and steal government information. Therefore, these cloud service providers (CSPs) need to be secure.
This begs the question: what is “secure” in this kind of context? FedRAMP is the authority that defines what security means and how it is achieved. FedRAMP exists in part to provide that centralized validation and, in part, to prevent the proliferation of different, varying standards that could duplicate government security efforts.
The specific act that created and enforces FedRAMP is FISMA, the Federal Information Security Management Act. If you’re curious, the actual text of the act can be found here. Honestly, though, reading the statements from the government isn’t terribly helpful.
More helpful are the specific definitions of security controls and policies maintained by NIST, the National Institute of Standards and Technology, under the framework NIST 800-53. This, you can read here.
In essence, FedRAMP has three goals:
- To set a specific set of standards for information security on cloud service providers to reduce duplication and inefficiencies in evaluating and upholding that level of security.
- To ensure that there’s a minimum baseline level of security to which all cloud service providers used by the government are held.
- To reduce friction and speed up the potential adoption of a new cloud service provider by a government contract; having certification means standards are met, and pre-audited to ensure FedRAMP compliance or that they are “FedRAMP ready”.
A lot goes into these standards. They encapsulate policies and requirements in access control, contingency planning, risk assessment, configuration management, standardization, and more.
FedRAMP certification is mandatory.
“Yes, FedRAMP is mandatory for all executive agency cloud deployments and service models at the Low, Moderate, and High risk impact levels. Please refer to the FedRAMP Policy memo for further information pertaining to FedRAMP’s applicability.” – FedRAMP.
For a cloud service provider to work with a governmental agency, they must receive an ATO for that agency, with or without previously having obtained a P-ATO.
Critical Terms to Know
Before digging much further, let’s provide a reference for the many acronyms that fly around in these kinds of documents.
There are already a few, but more will crop up, and it’s nice to have a resource to see what they mean at a glance.
- 3PAO – A 3PAO is a Third-Party Assessment Organization, an independent auditor that can evaluate a cloud service provider for adherence to FedRAMP standards.
- CSO/CSP – Cloud Service Offering/Provider. Companies that provide services, platforms, infrastructure, or other offerings on the cloud are cloud service providers.
- IV&V – Independent Verification and Validation Organization. This is a 3PAO, essentially, except it’s not on the validated list of 3PAOs maintained by FedRAMP.
- JAB – The Joint Authorization Board is the primary governance and decision-making body for FedRAMP. It consists of Chief Information Officers from the Department of Defense (DoD), the Department of Homeland Security (DHS), and the General Services Administration (GSA). You can learn more about it here. The JAB is responsible for issuing and accrediting P-ATO.
- PMO – The FedRAMP Program Management Office. This is the office that primarily governs P-ATOs and 3PAOs but also handles a lot of the standard business of the FedRAMP institution.
- SSP/SAP – System Security Plan and Security Assessment Plan. These are documents produced by the CSP and 3PAO respectively to present to FedRAMP PMO and agencies to obtain accreditation.
We’ll keep this list updated as new terms are introduced. You know how the government can be with renaming things and introducing new acronyms.
What Are the Differences Between ATO, P-ATO, and FedRAMP Certification?
These three terms are thrown around frequently amongst CSPs, but there’s often some confusion about what they mean and what the differences between them are.
First, FedRAMP Certification. This is a deprecated term that doesn’t have a truly specific meaning but can apply to both ATO and P-ATO. In essence, it’s the official stamp of approval by an auditor that says a cloud service provider meets the standards necessary to be allowed to work with government contracts.
An ATO is an Authority to Operate. This is the “path of least resistance” because it has a faster and less intensive process to complete. The CSP in question identifies an agency partner in the government that they would like to work with. The CSP and agency work with a 3PAO (Third Party Assessment Organization) that is qualified. More on that in a moment.
The cloud provider develops a system security plan and a list of the various policies, procedures and processes that the government agency would leverage to ensure safety and security of the cloud provider. The third-party assessor then evaluates the security standards of each of these security policies to a very granular level to audit the security of the cloud provider. If the audit passes – sometimes a long shot – the Authority to Operate is issued, and the government agency in question can start working with the cloud provider.
Note: This process is long and difficult. It’s very confusing; the documents produced can be thousands of pages long, and it can take months or even years to go through depending on the scale of the CSP and the agency and after all of that, it still has a high rate of failure. And yet, this is the least difficult path to FedRAMP certification!
The critical note here is that this is on a per-agency basis. If the same cloud service provider wants to work with another government agency as well, they need to go through the whole process over again for that new agency. While this can be somewhat faster than the first time – particularly because a lot of the work is already done – it still has to be taken step by step to attain a new ATO for that agency.
A P-ATO is a Provisional Authority to Operate. While the word Provisional might make you think it means it’s a lower-standard, faster, more streamlined option, it’s actually not really true. Or rather, it is, in a sense, but not the sense you might think.
P-ATO is a higher-standard form of FedRAMP authorization because it’s broader in scope. Instead of a narrow analysis of whatever a single agency would touch, the cloud service provider pursues a greater agency authorization to work with, broadly, any government agency. Instead of working with an agency directly, the cloud provider works with the Joint Authorization Board. The JAB itself provides the risk review of the paperwork provided by the cloud provider and has a 3PAO test, verify, validate, and analyze it. If the CSP passes, the JAB can then grant the P-ATO.
Note: The P-ATO does not automatically become an ATO when an agency decides it wants to work with a CSP. The agency still needs to go through the security authorization process to vet and provide the ATO; they just have the information much more readily available and pre-approved.
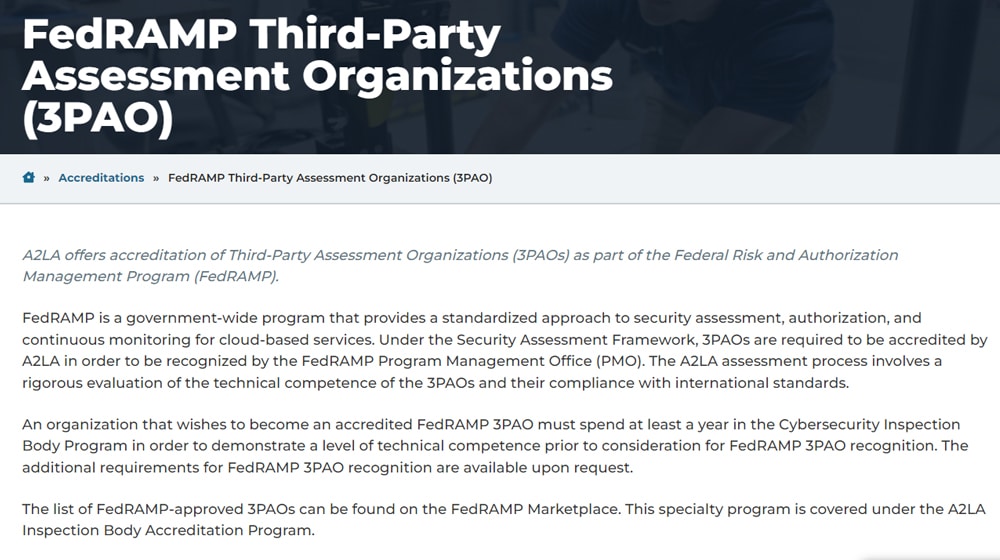
What is a qualified 3PAO?
Above, we mentioned that 3PAOs need to be vetted and authorized to provide appropriate auditing. After all, this is governmental security we’re talking about; having the government do it opens up room for corruption, but not having verification is even worse.
A qualified 3PAO is a 3PAO that has been accredited by the A2LA or American Association for Laboratory Accreditation. A2LA performs an assessment of the 3PAO and validates their independence and ability to provide an accurate, unbiased assessment of a cloud service provider. The specific requirements are specified under ISO/IEC 17020, along with specific FedRAMP knowledge requirements. More information on becoming a qualified 3PAO can be found here.
A 3PAO is also not qualified forever. Every year, A2LA performs a review of the company and must return a favorable review for the company to remain qualified. Additionally, every two years, A2LA needs to perform an on-site assessment akin to the original assessment to maintain validation.
Note: As of October 1, 2023, FedRAMP is increasing the requirements of their 3PAO teams. Any team performing work for an ATO must be made up solely of qualified personnel.
“Any 3PAO assessment deliverables containing work performed, prepared, or submitted by 3PAO personnel who do not meet the requirements for their role will be determined to be invalid, will be rejected, and will need to be redone by personnel who meet the required qualifications. FedRAMP will pursue corrective actions and possible removal of FedRAMP recognition if 3PAO deliverables and personnel do not meet these performance standards.” – FedRAMP Memo.
Integrating FedRAMP into the Cloud Computing Strategy
Cloud computing has significantly reshaped the landscape of data storage, processing, and management. This shift has forced the U.S. government and federal agencies to rethink their strategies concerning data security. The Federal Risk and Authorization Management Program (FedRAMP) emerged as a strategic response, ensuring that cloud services align with stringent security requirements.
One of the pivotal elements in the FedRAMP authorization process is the security assessment report (SAR). This report provides a comprehensive look at the cloud service provider’s risk posture, detailing vulnerabilities and required remediation actions. Often, the SAR is derived from a full security assessment and is an integral component of the authorization package.
Further emphasizing the depth of the process, a cloud service provider is expected to present its security package, which incorporates various templates and guidelines mandated by FedRAMP. A key feature of this package is the plan of action and milestones (POA&M), which outlines the provider’s roadmap for addressing any identified vulnerabilities. This POA&M is continually updated to reflect ongoing remediation efforts.
While the general FedRAMP requirements are grounded in the FIPS categorization of information systems, they are more specifically detailed in the NIST Special Publication 800-53. This publication sets forth a plethora of security requirements, which, when met, significantly bolster the security posture of cloud services.
The Joint Authorization Board (JAB) plays a crucial role, especially in the JAB P-ATO process. This provisional authorization is essentially an attestation of the cloud provider’s readiness to serve multiple federal agencies. In turn, individual agencies can use the JAB P-ATO as a reference, but they still conduct their own reviews, often culminating in an ATO letter, which grants the cloud provider explicit permission to operate within that agency.
Note: It’s worth mentioning that monitoring deliverables, which track a cloud provider’s ongoing security status and efforts, form a continuous backbone of the process. This ensures that even after an ATO or P-ATO is issued, the cloud service remains vigilant and adaptive to evolving threats and challenges.
Does a Cloud Provider Need a Qualified 3PAO?
You may have seen some hints that a qualified 3PAO is not necessarily required to receive an ATO. Is this true?
Surprisingly, yes. A P-ATO requires a 3PAO; a regular ATO can use what is known as an IV&V or Independent Verification and Validation organization. The IV&V is still held to the same kind of standards as a 3PAO; it’s just not on the list.
Speaking of the list – the list of qualified 3PAOs is found on the FedRAMP Marketplace site under Assessors, found here. Any company claiming to be an authenticated 3PAO needs to be on this list. We at Ignyte are proud to be on this list as a qualified 3PAO.
Are ATOs and P-ATOs Permanent?
Yes and no. They are not one-time assessments; while the full process to achieve either an ATO or P-ATO does not need to be fully repeated, the certification requires continual monitoring and auditing on a monthly and annual basis to be maintained.
For a P-ATO, the FedRAMP PMO handles this; for a regular agency ATO, the agency handles it.
How Ignyte Can Help
As a cybersecurity and compliance platform, we at Ignyte are proud to be able to offer our services as a Third Party Assessment Organization listed in the FedRAMP marketplace. We understand both the vast complexities of modern cybersecurity and the intricacies and details of the FedRAMP certification process.
More than that, we understand that any cloud services provider looking to work with the government will have to jump through hoops, develop extremely long documentation, and be subject to intense scrutiny. With such high standards – and a high risk of failure – this can make or break your potential government contracts.
What can we do to help?
- We know the work, what needs to be recorded and monitored, and how it can all be handled and compiled for both applications and regular compliance audits.
- We can automate much of the work, both to speed it up and to remove the possibility of human error.
- Our customized dashboard keeps a complete awareness of your qualifications and the state of your security at your fingertips.
Whether you’re a small CSP looking to work with a single agency and need an agency ATO, or you’re a larger company hoping to land multiple agency contracts and want to get a P-ATO, we can help. Just reach out today to get started!
Max Aulakh is a distinguished Data Security and Compliance leader, recognized for implementing DoD-tested security strategies and compliance measures that protect mission-critical IT operations. His expertise was shaped in the United States Air Force, where he was responsible for the InfoSec and ComSec of network hardware, software, and IT infrastructure across global classified and unclassified networks. He also developed strategic relationships with military units in Turkey, Afghanistan, and Iraq. After his tenure with the USAF, Max played a pivotal role in driving Information Assurance (IA) programs for the U.S. Department of Defense (DoD). As a Senior Consultant for a leading defense contracting firm, he led a team that ensured data centers met Air Force Level Security audits for regulatory requirements like HIPAA, SOX, and FISMA. Currently, as the CEO of Ignyte Assurance Platform, he is at the forefront of cyber assurance and regulatory compliance innovation, catering to defense, healthcare, and manufacturing sectors. Max is also an esteemed speaker, having presented at several conferences on topics including cybersecurity GRC, medical device security, and cybersecurity perspectives in vendor management. You can follow him in LinkedIn here.



 BLUF - Bottom Line Up Front
BLUF - Bottom Line Up Front