The overall defense industrial base is growing increasingly aware of the needs of modern information and cyber security. From recent major supply chain attacks to the constant threat of nation-state actors trying to compromise systems, it’s important to be committed to the best security you can implement, no matter where you are in the supply chain.
One of the tools provided to you, and required by the Defense Federal Acquisition Regulation Supplement, is the SPRS. SPRS is a score, and it needs to be kept up to date, but it’s also easy to overlook. So, let’s talk about what it is, when and why you need it, and how often you should update it.
 BLUF - Bottom Line Up Front
BLUF - Bottom Line Up Front
The defense industry faces growing cyber threats and requires strong security measures. The SPRS score, mandated by DFARS, assesses compliance with NIST SP 800-171 security controls. Contractors need to calculate and update this score, which ranges from -203 to +110, affecting DoD contract eligibility. Updating can be annual or as needed. SPRS doesn’t yet reflect NIST SP 800-171 Rev 3. Tools like Ignyte help track compliance effectively.
What is the SPRS Score?
SPRS, or the Supplier Performance Risk System, is a tool created by the Department of Defense as part of risk assessment and management. DFARS 252.204-7019, one of the many applicable regulations for the defense industrial base, requires that DoD contractors and subcontractors complete a self-assessment according to the security controls laid out in NIST SP 800-171.
If that sounds familiar to you, it’s the same NIST special publication used as the basis for CMMC to secure Controlled Unclassified Information.
The DoD provides a workflow for analyzing risk across the security controls outlined in NIST SP 800-171. The result of the workflow is a numerical score that is your SPRS score.
SPRS scores are semi-private. A business doesn’t need to publish its SPRS score, but they do need to submit it to the DoD via the Procurement Integrated Enterprise Environment system, which is maintained by the DoD itself. Only the company, the DoD, and a limited number of acquisition community members can see the score.
Why Does the SPRS Score Matter?
There are two reasons why the SPRS score matters.
The first is because DFARS says it does. In order to work with the DoD as part of the defense supply chain, you are beholden to the DFARS regulations, and that means you have to do what those regulations tell you to do, including calculating and maintaining your SPRS score.
The second reason is that it’s related to CMMC certification. While the SPRS score isn’t directly used in CMMC, both CMMC and SPRS are derived from NIST SP 800-171, which means that your SPRS score is reflective of your compliance with the security controls mandated by CMMC. If your score is out of line with where you should be in terms of your CMMC level, it’s a sign that something is wrong.
In general, the higher your score, the more secure you are and the more you can be trusted as a part of the defense supply chain. The lower your score, the riskier you are to work with, and the less likely you are to win DoD contracts.
Who Needs an SPRS Score?
Essentially, everyone who works with the government in any capacity that touches CUI.
More specifically, you’ll need to check your contract. But, there’s a good chance that your contract has a DFARS 252.204-7012 clause in it, which says something like “The Contractor shall provide adequate security on all covered contractor information systems subject to the security requirements in NIST SP 800-171.” You might also have a clause for DFARS 7019, which requires assessing your business against the same set of security controls.
Essentially, if you’re part of the government supply chain and you have anything to do with controlled information at all, you probably have to calculate and submit your SPRS scores.
How is an SPRS Score Calculated?
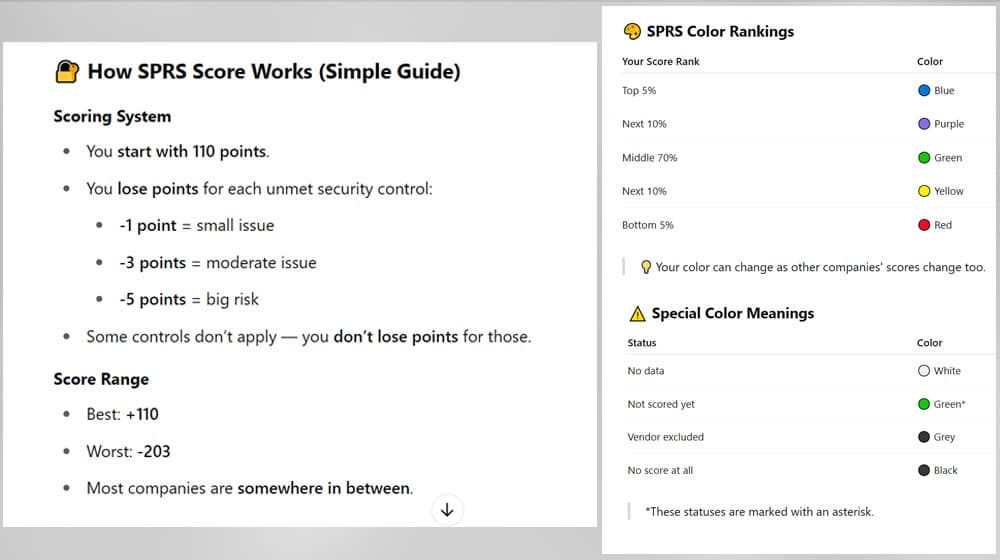
SPRS scores are subtractive scores. That means you start with a pool of points associated with each security control. You then go through and assess your compliance for each control, and for each one where you don’t meet the mark, you lose that point.
The trick is that you can lose more than one point per control.
- Limited impact failure is -1 point.
- Specific impact failure is -3 points.
- Significant risk failure is -5 points.
This means the range of score for SPRS runs from -203 to +110. The “perfect score” of +110 is the goal to strive for, though it can take several iterations and serious work to achieve. It’s also practically impossible to hit the full -203; you would have to have no security to the point where you’re probably not even functional as a business to hit that mark.
One quirk of the SPRS score is that certain controls can be “waived” if they aren’t applicable to your business. You aren’t penalized for not implementing something that is inapplicable to your operations.
More details can be found in the SPRS evaluation criteria manual, found here.
In addition to the numerical score, companies are assigned a color in the PIEE system. There are eight possible colors, and the color assigned to you will shift over time.
- The top 5% scoring companies are blue.
- The next 10% are purple.
- The next 70% are green.
- The next 10% are yellow.
- The bottom 5% are red.
Since this is a percentile scale, your position in the list will change based on the fluctuation of the scores of other businesses; if others improve and you’re left behind, your color can fall. If higher-scoring firms drop out, your color can rise. And, of course, changing your score can change your color.
Additionally, four other statuses are assigned colors. These four are also given an asterisk to note their special status.
- Firms with no scorable data are given white.
- Firms that are vendor-excluded are grey.
- Firms that have no score are black.
- Firms with scorable data pending but not yet scored are also green.
The color is less important than the numerical score; generally speaking, it’s just a way to see a percentile performance at a glance, and for the lowest-scoring firms to see a warning color and take action.
What is considered a good SPRS score?
With such a wide range, from -203 to +110, what do you need to be considered to have a good score?
This is actually contextual, and it depends in part on what level of CMMC or equivalent you need to achieve.
The best possible score is, of course, +110. This means you’ve successfully implemented everything in NIST SP 800-171. However, if you’ve ever gone through the analysis and seen everything you need to implement, you’ve probably encountered one fact: you don’t need to do that, almost ever.
In fact, only companies that need to achieve CMMC Level 3 need to implement all 110 security controls. Companies that are seeking Level 2 compliance only need around 88 controls, and Level 1 is even lower.
A number of years ago, an assessment of over 500 contractors with SPRS scores found that the average score of a first attempt was -27. It’s likely higher now since standards have increased, and it’s obviously higher for firms that have reviewed and implemented their POA&Ms, but it’s not entirely unlikely to encounter a relatively low initial score.
Generally speaking, the lower your score, the less likely you are to earn contracts. You represent a risk, increasing the lower the score is, and there are almost certainly alternatives to what you offer. You ideally want at least parity with your competitors.
How Often Does the SPRS Score Need to be Updated?
One of the most common questions we see is how often you need to update your SPRS score with the DoD.
Unfortunately, there’s no official guidance for this. So, generally speaking, you have three options.
Option #1: You can wait until someone asks for an updated score, and perform a new assessment to get it to them. Many businesses take this avenue, though it’s not without risks; if you’re operating on a tight deadline, the process for recalculating your SPRS score can be time-consuming enough to cause problems.
Option #2: You can check your contract and see what it says. Often, your contract will say how often you need to submit an updated SPRS score, which is probably going to be somewhere between once a year and once every three years (as in, in preparation for your once-every-three-years audit for CMMC).
Option #3: You can update it proactively as you make changes. This is a common choice for companies with relatively low SPRS scores; as you complete your POA&Ms to improve your security posture, you can also update and resubmit your SPRS score to have a better presence on the marketplace and with potential contracts.
There may also be additional circumstances that change how often you want to recalculate and update your SPRS scores. For example, because it’s a tangible and trackable metric, you might have executives who want to see improvement on that metric (even if they aren’t really sure what it represents or what improvement entails), so they might want something like monthly or quarterly progress reports.
Generally speaking, however, if your score needs improvement, you can recalculate it each time you’ve completed a POA&M; otherwise, you can simply recalculate it as often as necessary according to your contracts and other external factors.
Most firms will find that a minimum of once-a-year updates to their SPRS score is the sweet spot. You don’t re-do a lot of unnecessary work for analysis that doesn’t change frequently, but neither do you miss significant changes. And, if you implement more robust or more aligned security, you can update your score to reflect it and provide the benefits a higher score would bring.
Does SPRS Change with NIST SP 800-171 Rev 3?
Another question you might have is how SPRS scores change with the change in NIST SP 800-171.
SPRS score, as we mentioned, is derived from NIST SP 800-171; that special publication outlines 110 security controls, each of which has a point value in the SPRS score calculation.
Except, as you know, if you’ve read our guide to the transition between NIST SP 800-171 Revision 2 and Revision 3, this is no longer the case. The new NIST SP 800-171, Revision 3, only has a total of 97 security controls.
Does that mean that your SPRS score now only goes up to 97?
For now, no.
The fact is, NIST updated SP 800-171, but they kind of did it asynchronously with everyone else. Everything else that relies on NIST SP 800-171 was not prepared for the update; frameworks like CMMC and analyses like SPRS are not adjusted to make use of 800-171 Revision 3.
While this could become a point of friction, the DoD recently issued a memo establishing what is known as a Class Deviation. This deviation essentially says “yes, we know that 800-171 Revision 3 exists. For now, nothing supports it, so treat Revision 2 as the canon version until such time as we say otherwise.”
You can bet that, behind the scenes, the DoD and various organizations are working to develop newer iterations for things like SPRS and CMMC itself. For now, though, all of that is a work in progress, and until it’s ready, we’re still going to be using Revision 2 for everything that needs NIST SP 800-171.
That’s not to say that you should ignore Revision 3. It’s a good idea to be aware of it and know what the changes entail, so that when those changes do take effect, you’re prepared to implement them and change your reporting to match. Just don’t jump the gun and find you’re doing more harm than good by not playing by the rules as written.
How Ignyte Can Help
Where do we come in?
Tracking your SPRS score requires monitoring all of the NIST SP 800-171 security controls according to the assessment methodology provided by the DoD and NIST. In addition to the overall process of creating your SSP and creating/implementing POA&Ms, there’s a lot of record-keeping and data tracking that goes on with this score.
To that end, the Ignyte Assurance Platform can definitely help. As a centralized, collaborative, non-siloed system for tracking compliance across a wide range of different security frameworks, we’re well-positioned to help you keep tabs on your SPRS score, including tracking changes as they happen.
If you want to see what the Ignyte Platform can do for you, just book a demo today to get started, or reach out with any questions you may have.
Max Aulakh is a distinguished Data Security and Compliance leader, recognized for implementing DoD-tested security strategies and compliance measures that protect mission-critical IT operations. His expertise was shaped in the United States Air Force, where he was responsible for the InfoSec and ComSec of network hardware, software, and IT infrastructure across global classified and unclassified networks. He also developed strategic relationships with military units in Turkey, Afghanistan, and Iraq. After his tenure with the USAF, Max played a pivotal role in driving Information Assurance (IA) programs for the U.S. Department of Defense (DoD). As a Senior Consultant for a leading defense contracting firm, he led a team that ensured data centers met Air Force Level Security audits for regulatory requirements like HIPAA, SOX, and FISMA. Currently, as the CEO of Ignyte Assurance Platform, he is at the forefront of cyber assurance and regulatory compliance innovation, catering to defense, healthcare, and manufacturing sectors. Max is also an esteemed speaker, having presented at several conferences on topics including cybersecurity GRC, medical device security, and cybersecurity perspectives in vendor management. You can follow him in LinkedIn here.



 BLUF - Bottom Line Up Front
BLUF - Bottom Line Up Front