The final step to achieving ISO 27001 certification is passing a final audit of your ISMS. During this process, you will work with an external, third-party auditor to perform a thorough audit of your systems, to evaluate compliance with the guidelines in ISO 27001. The question is, what will that auditor be doing? Do you hand them paperwork and the keys to the building and let them do their thing, or are they more interactive? What can you expect when working with your auditor?
For the purposes of today’s post, we’re talking specifically about the external audit conducted by a certified third-party auditor. Internal audits are also important, but because they’re internal, you will have more of an idea of what to expect because you set up the auditing team.
 BLUF - Bottom Line Up Front
BLUF - Bottom Line Up Front
The final step to achieve ISO 27001 certification involves passing a two-stage external audit by a certified third-party. Stage one focuses on comprehensive documentation review, while stage two involves hands-on evaluation of ISMS implementation. Auditors check compliance with ISO 27001 guidelines through document submissions, employee interviews, and evidence validation. If nonconformities are found, they must be resolved before certification, with minor ones addressed by the annual surveillance audit. Efficient documentation management is key in passing the audits.
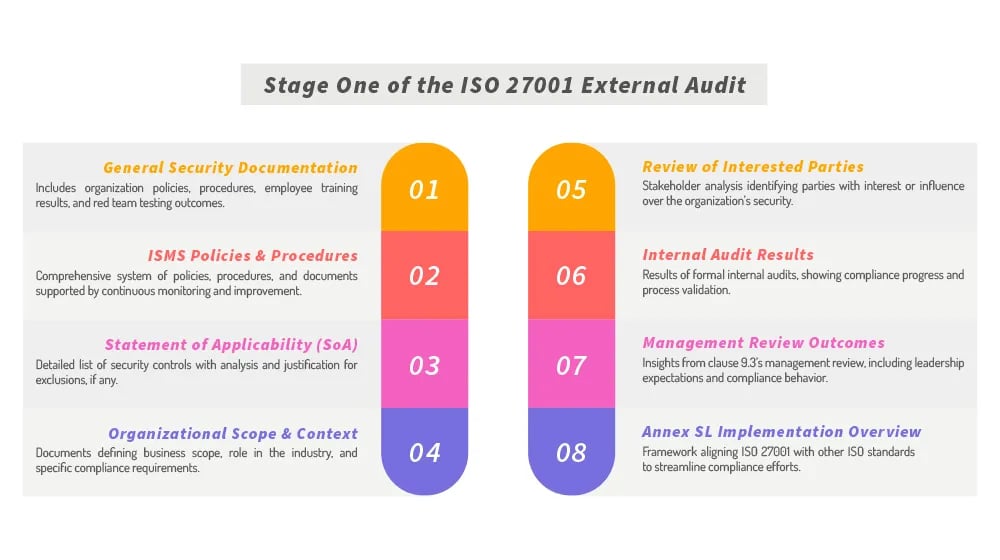
Stage One of the ISO 27001 External Audit
The external audit takes place over two stages. The first stage is, essentially, a thorough documentation review. Your auditor will ask you for the relevant documents you will have put together as part of your ISO 27001 preparation. There’s a lot that goes into this, though if you’ve been following our ISO 27001 checklist, you should have it all on hand.
What will the auditor request and look through?
General company documents relating to security. There are a ton of documents that go into ISO 27001 as part of your ISMS and the supporting documentation. Everything from organization policies and procedures to the results of employee training and red team testing may be included in this packet of documentation.
Keeping track of all of this documentation across the many months it takes to develop and implement it can be tricky. That’s why we developed the Ignyte Platform. Our platform is a secure, compliant, and collaborative location for storing and managing documentation for various frameworks. It won’t do everything for you, but it will make it much easier for you to keep track of what has and hasn’t been done, as well as collaborate throughout your organization without the risk of inappropriate versioning or overwritten data from siloed, individual software.
ISMS policies and procedures. While we frequently talk about the ISMS as a single thing, it’s actually just a complex system of policies, procedures, and documentation supported by continuous monitoring and improvement. It’s those documents that are the critical part here. You can learn more about what goes into an ISMS here.
Your Statement of Applicability. Your Statement of Applicability, or SoA, is a document created as part of your initial forays into ISO 27001. It is essentially a complete list of each of the security controls outlined in ISO 27001, with an accompanying analysis of what the control is and how it applies to your business. In the rare event that a control does not apply, this is the place where you state that as justification for why you don’t have anything implemented for that control.
Your auditor will review this document closely and determine if your justifications apply. If some controls are found to be too narrow or too broad, or you waive controls that would apply, the auditor will point these out and likely end the audit until they’re fixed.
Your organization’s scope and context. These are somewhat less formalized documents that accompany other documents and help define the overall scope, position, and role your business plays in the industry, which can affect how stringent your requirements are.
A review of interested parties. This is an analysis of stakeholders, business partners, and people who have an interest or influence over your business, which can be a part of security through the use of that influence.
Internal audit results. Internal audits are a key part of the ISO 27001 process, and they are rather formalized to ensure that they are thorough, done using an impartial judge, and validate your security posture. The results of these audits – even failed audits from early in the process – can help your auditor see your internal processes and your progress in compliance.
Results of your management review. Another critical part of ISO 27001 implementation is a review of management. The review’s scope and process are outlined in clause 9.3 of ISO 27001 and review many elements of management behavior, expectations, and compliance. This is also a common point of failure; management that doesn’t take ISO 27001 seriously will jeopardize compliance.
Overview of Annex SL implementation. Annex SL is a framework developed to act as an underlying structure to help businesses achieve compliance across multiple ISO standards, including ISO 9001, ISO 14001, ISO 45001, and ISO 27001. It’s essentially the center of the Venn diagram of requirements across each of these standards; by complying with Annex SL, you can avoid duplicating work across multiple ISO standards.
Overall, the goal of this phase of the audit is to make sure that you have all of your documentation in order and that your overall system is designed to the specifications of ISO 27001 and its related documents. Key elements like your overall risk assessment, your business objectives, and your scope need to be thoroughly and properly defined, and your auditor will check them.
On a more tangible level, how is this stage of the audit conducted? It starts when you confirm a contract with an auditor, and they request documentation. You submit your paperwork (generally digitally), and they will review it.
A secondary, but no less important, part of the first stage of the auditing process is a series of interviews with key personnel. Generally, this means your top management, including your C Suite and directors, as relevant to your organization. These interviews aren’t necessarily very long, but they are very important; your auditor will be looking for specific knowledge, awareness, and training and will be assessing the level of management buy-in and overall organizational support for ISO 27001 implementation.
More than one organization has failed the audit at this stage through inattentive or poor management buy-in.
The overall goal of stage one is a filter; if there are failures with regards to key elements of ISO 27001, whether in management buy-in, something you specified in your Statement of Applicability that the auditor disagrees with, or missing documentation, the audit may effectively end here. Missing documentation can be located and handed over, but it’s still a warning sign if you don’t have it on hand when it’s asked for.
The good news is that this stage is frequently done remotely, and since it’s largely a matter of documentation review and phone calls, there’s relatively little waste in the event of a failure. If your organization fails, your auditor will describe why, and you will have an opportunity to fix it. If you pass, the second stage of the audit will be scheduled.
One thing to note here is that different auditors have different focuses. Some will be more concerned with the overall status of your ISMS and the organization of your documentation. Others pay attention to small details, even down to the formatting of certain documents. If the density of detail and critique of otherwise meaningless details prove to be too much of a roadblock, finding a different auditor may be appropriate.
Stage Two of the ISO 27001 External Audit
If your organization passes stage one, your auditor will schedule stage two, usually for 1-3 weeks after stage one.
This is where the more hands-on analysis of your ISMS comes into play. Your auditor and their team will review evidence of how you’ve applied controls throughout your organization.
They do this in many ways:
- They will conduct interviews with your employees, looking for their awareness of their responsibilities with regard to the company policies, the ISMS, and ISO 27001. For key personnel who have specific requirements, those will be analyzed as well.
- They will examine the records that verify compliance across various ISO 27001 security controls. This isn’t the theoretical documentation from stage one; it’s more like audit logs and other proof.
- They will get hands-on with specific controls and their implementation. For example, they might test encryption for data storage across company devices or check for MFA across user accounts.
One critical element of this stage of the audit is that it uses statistical sampling rather than a thorough review. If your company has 100 laptops that need to have encrypted data storage drives, your auditor will randomly pick a handful of those laptops to verify.
This sampling method is all but required to make the job of the auditor feasible at all. The larger the organizations, the more impossible it would be to check every single device. The random selection and statistical sampling method allow for a relevant review without needing to examine every grain of sand on the beach.
The process and standards of this stage of the audit are governed by another ISO standard, specifically, ISO 19011, the Guidelines for auditing management systems standard. You and your organization don’t need to know what’s in this standard, only that your auditor will be using it.
Your auditor will also likely evaluate external relationships here as well. If your business works with suppliers, your auditor will examine your relationship with them, your contract, any NDAs in effect, and so on.
Most of the time, stage two of the audit is conducted in person. As such, your auditor will also evaluate things like physical security, evacuation plans, disaster recovery plans, and other such elements of business continuity. This will be fairly detail-oriented, and you can expect them to look for things you might not even think of. If you’ve ever seen a picture of a server hanging precariously over a utility sink, that’s the kind of thing that can fail an audit.
Some companies don’t have physical locations. In these cases, the audit will be conducted remotely because physical security doesn’t need to be assessed.
What Happens if Your Auditor Finds a Nonconformity?
Throughout the audit process, the ideal result is that everything is in order and that you pass your audit. It is vastly unlikely for this to happen on the first go-around. Minor nonconformities won’t necessarily result in a failure of the audit, but more major or significant nonconformities can and will require remediation.
If your auditor identifies a nonconformity, they will explain the nature of the nonconformity to you. They may, for example, tell you that there’s a gap in coverage for a given security control in a given process in your business or that the results of that analysis of 100 laptops found that some of them didn’t have encryption implemented.
What the auditor will not do is tell you how to fix it. It’s not their job or responsibility to lead you to compliance; it’s only their job to evaluate your status. That said, some auditing firms have secondary teams to help with implementation; if your auditor finds issues, they can refer you to the secondary team. Be aware that this may jeopardize the auditor’s ability to perform the audit again, as they will no longer be an impartial party.
Major nonconformities need to be resolved before a certificate can be issued. Minor nonconformities will not prevent you from getting your certificate, but they are added to a list of things that need to be fixed by the time your annual surveillance audit is conducted. If they are not resolved by that audit, it can be grounds for failure and expiration of the certificate.
Helping Pass the Audits
If your business is starting the process of achieving ISO 27001 certification, it’s critical that you keep all of your documentation in order. There are many different ways you can do this, but we’ve found that one of the best is to use a platform designed specifically for managing the documentation associated with security frameworks. That’s why we put together the Ignyte Platform: to help businesses keep all of their relevant documents in one place, up to date, and accessible to the people who need to be able to access them.
If you have any questions, or you would like to book a demo and see what Ignyte can do for you and your ISO 27001 journey, feel free to reach out.
Max Aulakh is a distinguished Data Security and Compliance leader, recognized for implementing DoD-tested security strategies and compliance measures that protect mission-critical IT operations. His expertise was shaped in the United States Air Force, where he was responsible for the InfoSec and ComSec of network hardware, software, and IT infrastructure across global classified and unclassified networks. He also developed strategic relationships with military units in Turkey, Afghanistan, and Iraq. After his tenure with the USAF, Max played a pivotal role in driving Information Assurance (IA) programs for the U.S. Department of Defense (DoD). As a Senior Consultant for a leading defense contracting firm, he led a team that ensured data centers met Air Force Level Security audits for regulatory requirements like HIPAA, SOX, and FISMA. Currently, as the CEO of Ignyte Assurance Platform, he is at the forefront of cyber assurance and regulatory compliance innovation, catering to defense, healthcare, and manufacturing sectors. Max is also an esteemed speaker, having presented at several conferences on topics including cybersecurity GRC, medical device security, and cybersecurity perspectives in vendor management. You can follow him in LinkedIn here.



 BLUF - Bottom Line Up Front
BLUF - Bottom Line Up Front