 BLUF - Bottom Line Up Front
BLUF - Bottom Line Up Front
CMMC is a cybersecurity framework for DoD contractors to protect Controlled Unclassified Information (CUI). It involves five levels of compliance assessed by a third-party auditor. Costs depend on organization size, with strategies to reduce expenses through automation. The audit process includes determining scope, assessing controls, and closing deficiencies. Preparations involve defining CUI scope, applying NIST 800-171, and developing specific policies. Positive audit outcomes require readiness and expert guidance.
Introduction: What is CMMC Audit and What are the CMMC Requirements?
Business owners whose revenue streams depend significantly or partially on government contracts have been recently faced with the mandatory emerging regulations called Cybersecurity Maturity Model Certification, also known as CMMC. All organizations working with the Department of Defense (DoD) and Federal government as their prime or subcontractors must be audited against these requirements by a competent third-party CMMC auditor.
Even though these CMMC guidelines are new, they are just an enhanced program of the DoD’s initiative to strengthen already known frameworks in the supply chain risk management domain such as NIST SP 800-171 and Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012.
In this article, you will learn about the CMMC audit process, who can perform one, what are the CMMC requirements, efforts, and costs are associated with your progress toward a CMMC preliminary assessment, and eventually full CMMC compliance.
What is CMMC?
CMMC is an industry and government-driven framework created to respond to risks and threats that can impact the Defense Industrial Base (DIB) affiliates and the entire supply chain during research, design, and development processes. The objective of this certification is to ascertain that all DoD contractors implement business level and security safeguards for protecting Controlled Unclassified Information (CUI) against data exfiltration and breaches.
CUI has a very broad definition and includes but is not limited to any tangible results of defense contractors’ collaboration. For example, the classification of CUI could include program specifications and requirements, blueprints, technology, equipment performance indicators, or other details of defense products manufacturing and logistics.
In addition, CMMC provides guidelines to verify the implementation of cybersecurity safeguards for maintaining cyber hygiene across the contractors’ DIB suppliers.
What is a CMMC Audit?
A CMMC audit is the process of assessing an organization’s cybersecurity maturity. It is also a prerequisite process required to demonstrate an organization’s compliance with the desired CMMC level before being certified.
CMMC provides five compliance levels used to match contractors’ risk profiles to the data they use, store, and transmit. Level 1 indicates the lowest rating in the cybersecurity program and implementation of security controls, and Level 5 represents the highest maturity rating. While the first level is a must-have for all companies working with the DoD, the majority of government contracts will require Level 3 and higher from their prime and subcontractors.
Who performs a CMMC Audit?
CMMC requires all 300,000 DoD contractors to get audited and obtain certification from a trusted and approved third-party assessment organization (C3PAO). While the CMMC Accreditation Body (CMMC-AB) is responsible for reviewing audits and issuing certificates, C3PAO must perform an audit. Ignyte, being one of the entities approved as a Candidate Maturity Level 3 CMMC Assessment Organization by the CMMC-AB, will be able to audit organizations from various industries, and automate the audit process to reduce the associated costs.

Costs Associated with CMMC Audit Preparation
The CMMC audit cost depends on the size of an organization. Notably, Companies should expect to incur the following costs in a CMMC audit process:
- Audit preparation costs: Also referred to as soft costs, audit preparation costs are the expenses for preparation and external consultancy. They range between $15,000 and $100,000 depending on the CMMC level and other factors.
- Hard costs: Hard costs are also incurred in audit preparation and the audit process. In the former, hard costs involve investments made in processes needed to meet audit requirements and range between $20,000 and $60,000. They include costs for implementing authentication mechanisms, endpoint security, and log monitoring. On the other hand, the hard costs for completing a CMMC audit process range between $10,000 and $40,000.
*For a more detailed overview of costs associated with CMMC audit preparation, read our article on Ignyte Institute.
CMMC Audit Cost Reduction Strategies
Ignyte fundamentally believes in automating all aspects of CMMC to reduce audit costs and manage ongoing cybersecurity efforts internally within your organization. The Ignyte platform includes several key modules and capabilities targeted towards reducing manpower and time spent on audits.
CMMC Audit Process – The Approach
As previously stated, contractors aspiring to win future DoD contracts must first prove they have been certified to any CMMC levels. In this case, a C3PAO performs an on-site, evidence-based assessment to demonstrate a contractor has achieved cybersecurity capabilities defined in one of the CMMC Levels. The CMMC audit process comprises of the following steps:
- Step 1 in CMMC Audit Process: Business Scope Determination
When an organization has hired a C3PAO, one of the tasks is to quickly identify the entity under inspection. Federal contractors often hold multiple companies under a complex structure with multiple Commercial and Government Entity Program (CAGE) codes. It is critical for the assessor to determine the exact entity under inspection. Many Organizations Seeking Certification (OSCs) may not be aware that the CMMC certification is an entity-level certification, not just a systems-level technical certification.
The business scope can also be defined around a specific line of business or business unit dedicated to conducting federal opportunities. Upon determining the entity structure, the next step is to clearly identify the technical scope. If you have any questions regarding your entity structure and how it impacts the CMMC certification, please contact Ignyte’s Legal team to help you through this process.
- Step 2 in CMMC Audit Process: Technical Scope Determination
The technical scope is formally known as the “Authorization Boundary” in similar government certification schemes such as FedRAMP. This is the most complex part of the whole process. Technical scoping can mean many things, depending on how knowledgeable an auditor is and their formal training and background. Your boundary may include the entire organization if you are a small business, including laptops and desktops, or it could include a subset of your network.
Having a clear diagram explaining the rationale and justification about the boundary is a great starting point. The Ignyte Platform is often used by intelligent organizations to completely automate the discovery of your boundary and maintain scope over your technical boundary. It is essential to understand that your boundary may contain several devices outside your Azure cloud environment, such as printers, laptops, and data backups.

- Step 3 in CMMC Audit Process: Reviewing current and existing corporate cybersecurity programs
The C3PAO coming into your organization must understand the nature of your business in context with existing cybersecurity protection schemes and similar certifications. This includes simplified regulations such as International Traffic in Arms Regulations (ITAR) to more stringent requirements such as Risk Management Framework (RMF) variants, including classified facilities with program-specific Joint Special Access Program Implementation Guide (JSIG) requirements.
Often, teams of professionals working within the organization are required to use the same tooling and technology to satisfy a multitude of compliance schemes. Mapping various requirements to a common set of technologies and frameworks is a great way to reduce the cost of implementing cybersecurity certification programs. For example, Security Technical Implementation Guide (STIG) level hardening is one of the best-kept secrets in our industry. Ignyte helps with Security Content Automation Protocol (SCAP) and STIG programs across organizations, allowing businesses to re-leverage the same technical data from one scheme to another.
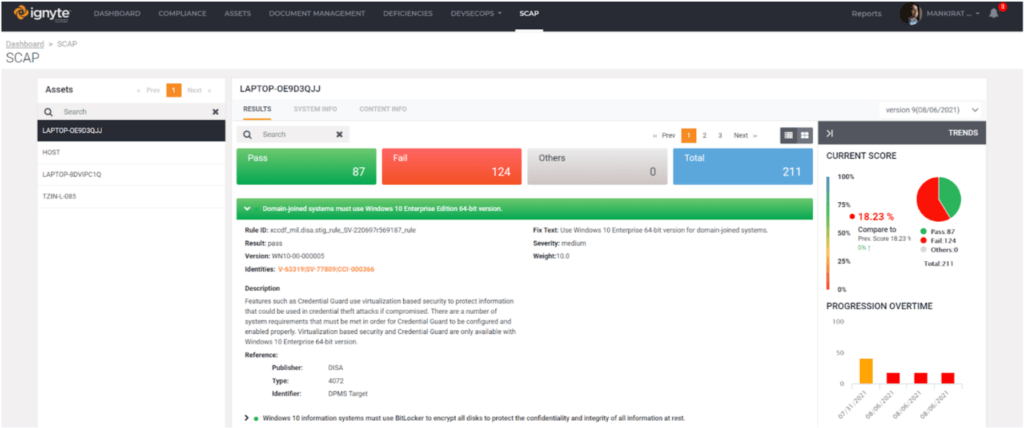
- Step 4 in CMMC Audit Process: Reviewing currently implemented cybersecurity controls
As of this writing, the concept of the Security Assessment Plan (SAP) from other federal security compliance schemes has not yet been leveraged by the CMMC-AB. However, the concept still applies to ensure the audit is conducted pragmatically. A plan should be formalized by the C3PAO. No audit should be a surprise to any organization and a good plan provides key information to the OSC. Review of controls should be very straightforward using approved test cases from the CMMC-AB and NIST 800-171 Assessment Guide. The controls review should be centered around your technical scope, where much of your CUI is stored, transmitted, and managed.
- Step 5 in CMMC Audit Process: Verifying the implementation of the cybersecurity controls
After ascertaining that required security controls are in place, the C3PAO then evaluates each control in-depth. Although the previous steps demonstrate the controls are in place, verification is vital as it demonstrates correct implementation and deployment of each control. Here the assessor may choose to sample a certain type of testing known as `Methods and Test Objects’, this includes interviewing, reviewing, or conducting an actual technical test on your boundary to determine if the control has been properly implemented.
Control auditing requires the auditor to be intelligent and knowledgeable about a multitude of processes and technologies. It is important to conduct proper due diligence into the background of the auditor to ensure they understand the fundamentals of corporate risk management and have worked within DoD certification schemes.
- Step 6 in CMMC Audit Process: Review of current POA&Ms & potentially generating new POA&Ms
An experienced cybersecurity professional fundamentally knows that no system can truly exist without some level of deficiency. An astute auditor can also find inconsistency within documentation when examining your technical environment. In the DoD scheme, these deficiencies are known as Plans of Actions and Milestones (POA&Ms).
POA&Ms are important because they allow an organization to plan for technology through normal business lifecycle events such as the end of life technology upgrades and implementing more expensive controls in consideration of business growth. They are essential for proper planning and make the cybersecurity experience realistic. As of today, the CMMC-AB has provided guidance that no POA&Ms should be open prior to inspection and all POA&Ms must be closed before you are awarded certification. The bottom line is that you must select an auditor who is experienced in both risk management and DoD schemes to help you navigate complex scenarios.
- Step 7 in CMMC Audit Process: Issuance of the certification
Upon closure of POA&Ms, the audit report and certification are the final steps in a CMMC audit process, where the C3PAO issues an official report to the CMMC-AB. After performing internal quality assurance, the C3PAO submits the audit report that describes the performance of an audited company. In particular, the submitted audit report details whether the organization meets the cybersecurity requirements stipulated at the target CMMC level. In addition, the report enables the CMMC-AB to perform its own quality assurance to validate the audit assessment results.
Only then can the CMMC-AB determine if the organization qualifies for a CMMC certification. When issuing the official audit report, the C3PAO keeps the results confidential to protect the organization from suffering reputational damage if the findings show it has not achieved DoD audit readiness status.
What is the Outcome of the CMMC Audit?
An audited company should expect to receive a report from the CMMC-AB regarding its CMMC capabilities. The report often contains detailed notes regarding the tested environment. The positive outcomes of the CMMC audit include detailed findings of the assessed controls. Through the findings, an organization can determine whether it has achieved the recommended cybersecurity capabilities required to win a contract with the DoD.
On the other hand, the outcomes can be negative if the findings demonstrate control deficiency or failure. In such an audit scenario, the organization’s failure hinges on several factors. For example, a failed control may imply that a lack of implementation can impact the business due to potential loss of CUI and may require the organization to implement compensating controls. Also, control failure may be an isolated occurrence but may call for additional examination work to determine if the failure is systemic organization-wide.
How to Prepare for a CMMC Audit to Make Sure You Get a Positive Result
Using a CMMC audit checklist and NIST 800-171 A is the most effective way to prepare for an audit to get a positive result. If you are a seasoned expert, try supplementing your strategy with NIST 800-53 for additional clarity and content on properly interpreting the control. The following is a simple seven-step CMMC audit checklist that can assist organizations in preparing for a successful audit:
- Define the CUI scope clearly
The initial step in preparing for a CMMC audit is establishing locations where a company stores, processes, and transmits CUI. Knowing its CUI enables an organization to design its NIST 800-171 policies, services, and processes properly and specific to its business. Furthermore, the government contracting official for prime contractors must define the CUI for all subcontractors. Check your contracts, markings on drawings, and other documents to understand where CUI may be flowing.
- Determine the applicable NIST 800-171 and CMMC Level controls
After understanding the CUI environment, an organization can now identify the processes, systems, or services within the NIST 800-171 scope. Remember the CMMC scheme is fundamentally built on NIST 800-171 guidance. For companies with simple networks, the applicability of controls may apply across the entire network. However, for organizations whose CUI environment is in segmented networks, the controls apply to only the appropriate network segments.
- Create organizational specific policies & procedures for addressing compliance requirements
Different contractors have various risk levels. In this regard, policy, procedures, and standards may change according to internal and external cyber risks. Therefore, determining the different cybersecurity compliances applicable to an organization, such as industry-specific laws and international or domestic privacy regulations, is a crucial audit preparation aspect. Once identified and developed, the company must document the requisite procedures, controls, standards, and policies used to inform various management decisions. Don’t just copy a template and expect an auditor to pass you with flying colors. Your documentation needs to be specific to your business and scope.
- Operationalize the created policies
Policies provide management intentions, while controls provide direct guidance on how to operationalize policies into step-by-step procedures. Policies are often written and then forgotten. Don’t let this mistake happen to you. For a successful audit, your policies must be demonstrated through knowledge, underlying procedures, and playbooks. Therefore, it is essential to define and identify the teams and individuals responsible for specific controls around your CUI. Assigning specific controls to particular teams and team members ascertains that all required controls are being followed accurately and not overlooked due to miscommunication concerning the assigned responsibilities.
- CUI environment documentation
All auditors will immediately gravitate towards your System Security Plan (SSP) section containing CUI identification and POA&Ms. The SSP answers questions like why, where, what, who, and when and contains information regarding various processes, technology solutions, and people within a CUI environment (your scope). On the other hand, POA&Ms detail the NIST 800-171 control deficiencies. Failing to have both documents in pristine condition will most likely result in immediate audit failure. Preparing these two artifacts centered around your scope and business boundary containing CUI is absolutely critical.
- Assess maturity and risk across business and technology processes
By leveraging risk frameworks such as OCTAVE, NIST 800-37, ISO 31010, and FAIR, a company can assess how well it has implemented cybersecurity risk management and the extent it has reduced risk to CUI. It is up to the organization to determine which controls or a combination of controls to use. As we mentioned earlier, an astute auditor can always find issues, and no technology system exists truly without deficiencies; therefore, it is critical to demonstrate fundamental knowledge of proper risk management. Complementing your 800-171 strategy with additional frameworks can formalize this risk-based decision-making.
- Identify improvement areas by using control execution metrics
Upon implementing all controls, a company must monitor them continuously to identify areas requiring improvement and optimization. Monitoring should be an ongoing process as it highlights the areas where a company can improve security. Creating Key Risk Indicators (KRIs) and Key Performance Indicators (KPIs) can help highlight such areas. Metrics around your security program can provide leading indicators of potential problems. Metrics also provide the auditor a sense of comfort that there is the proactive management of controls within an organization. Ignyte platform is used to build and drive decision-making through key metrics for your entire security program, including CMMC.

Next Steps
A CMMC audit can be a daunting task for both small and large organizations. We aim to drive efficiencies and effectiveness on implementation and audit performance leveraging automation. Contact us today to speak to a DoD-trained professional on all forms of security audits, including CMMC, FedRAMP, or more stringent requirements around your classified environment, such as JSIG SCA requirements automation.
CMMC audit certification is mandatory for all DoD contractors, and therefore wise to prepare for a positive outcome with the help of an expert. Ignyte is one of the best companies to assist organizations in preparing for an audit and guiding them through the audit process.


