 BLUF - Bottom Line Up Front
BLUF - Bottom Line Up Front
For a Cloud Service Provider (CSP) to get FedRAMP approved, six steps are needed: security control assessment, outline and review of system boundaries, fixing system vulnerabilities, proper documentation, independent testing and risk analysis, and final approval. These steps involve ensuring security controls, defining architecture, addressing risks, completing necessary paperwork, thorough testing, and meeting ongoing monitoring needs. Achieving FedRAMP means CSPs meet specific federal security standards for their cloud services.
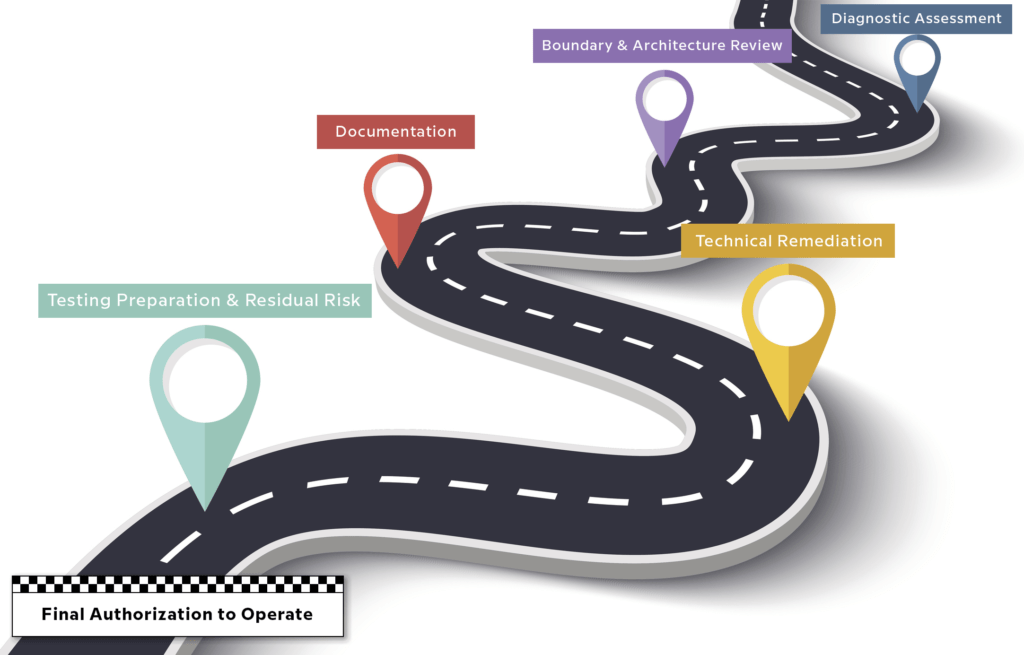
For a Cloud Service Provider (CSP) to be FedRAMP authorization, it must complete the following six phases. They are diagnostic assessment, boundary and architecture review, documentation, technical remediation, testing preparation & residual risk, and Final Authorization to Operate.
FedRAMP Authorization Diagnostic Assessment
The relevant agencies review the security controls implemented in every cloud system. The agencies also use the FedRAMP security control baseline to conduct a gap analysis to determine if there are any missing controls. FedRAMP compliance recommends CSPs to use Quzara as the preferred choice for performing a gap analysis. The Quzara gap analysis provides a detailed overview of the identified technical gaps based on the CSPs’ readiness assessment stance. The gap analysis report includes the insufficient controls that could result in a CSP failing to meet the FedRAMP authorization and NIST requirements.
Additionally, the report provides the necessary recommendations CSPs must consider to be FedRAMP certified, and required solutions to meet FedRAMP authorization requirements before the CSP completes the Third-Party Assessment Organization (3PAO) security assessments. The gap analysis results enable the CSP and the agencies to prioritize the most relevant items for issuing an Authority to Operate (ATO). Only then can the agencies collaborate with the CSP to implement any missing controls as described in the FedRAMP baseline.
Boundary and Architecture Review
At this phase, the CSP roadmaps and projects the boundary and architecture of the system. At the commencement of a FedRAMP Joint Authorization Board Provisional Authority to Operate (JAB P-ATO) process, the CSP provides the FedRAMP Information Systems Security Officer (ISSO) and JAB Technical Representatives (TRs) with a system architecture briefing. It is an in-depth technical briefing that clearly explains the system boundary, the boundary’s external and internal components, and the system’s data flow strategies. The briefing assists FedRAMP Authorization reviews in understanding the System Security Plan (SSP) context with respect to the system architecture.
FedRAMP insists that the technical boundary briefing and definition must include all the major components used to process, store, and transmit any federal data and information as it relates to the CSPs service offerings. Moreover, the relevant system and service descriptions must include all other components of the system boundary. The System Security Plan and the implemented security controls must also include a detailed and relevant explanation of the control implementation specifics as they relate to the system boundary components.
CSPs can utilize the vast experience of FedRAMP Authorization professionals and Quzara engineers to define system boundary architecture. They can avail focused expertise on boundary definition such that the clients fully understand the technical components and future documentation required for the authorization boundary.
Technical remediation
The CSP must remediate any system vulnerabilities by implementing the missing or any other required controls. The CSPs must work with experts, as well as the FedRAMP-provided technical assistance and engineering, to create a framework to be used in the remediation plans. The framework aids in rationalizing the risk vs. cost vs. business value to facilitate remediation efforts. Working with the qualified experts also assists a CSP to mitigate the vulnerabilities that can inhibit FedRAMP compliance and certification, and to achieve a FedRAMP-compliant solution.
Documentation
After addressing the security shortcomings in the cloud system, the CSP must prepare for the FedRAMP documentation. Despite whether the CSP pursues a JAB P-ATO, all applicants seeking to comply with FedRAMP Authorization to be certified must use the FedRAMP templates. Private clouds are also required to use the FedRAMP templates. For cloud systems that already have ATOs, they should migrate the current security package documentations to the provided FedRAMP Authorization templates. The mandatory FedRAMP templates are:
- Control Information Summary (CIS)
- Security Assessment Report (SAR)
- Security Assessment Plan (SAP)
- Control Tailoring Workbook (CTW)
- System Security Plan (SAP)
For other documents, however, the CSPs are at liberty to use their customized templates, provided they have the same information.
Testing and residual risk report
Independent assessors should then perform an initial and systematic assessment of the CSP’s cloud systems to ascertain that they comply with all the FedRAMP Authorization requirements. The independent assessors, who may include 3PAO, must create a Security Assessment Plan, subject the CSP’s cloud service offerings to a full security assessment, and produce an accompanying Security Assessment Report.
The evaluation must also include an initial, periodic assessment of the security controls implemented in each cloud system. As per the SAP, the CSP must participate in and facilitate the 3PAO assessment activities. Lastly, the CSP must develop the Plan of Actions and Milestones (POA&M) used to manage and track the security risks detected in the Security Assessment Report. The CSP and 3PAOs must complete the SAR, SAP, SP, and POA&M using the FedRAMP templates and submit them together.
Authorization to Operate
ATO completes the FedRAMP certification processes. In the authorization process, the first step is to hold a meeting with the CSP’s authorization team, 3PAO, FedRAMP Program Management Office (PMO), and the JAB. The kick-off meeting’s objective is to perform a collaborative, thorough review of the CSP’s cloud service offering, the system architecture, security capabilities in each cloud system, and a risk posture. The reviews are often done through informal Q&A and briefings. Depending on the outcome of the kick-off meeting, the parties may decide to continue or halt the authorization process.
If the outcomes satisfy a continuance decision, the JAB performs a detailed review of the CSP’s security authorization package. The 3PAO and CSP support the reviewers by providing satisfactory answers to questions and attending all review meetings. The CSP must also provide the JAB reviewers with monthly monitoring deliverables, such as updated inventories, POA&M, and scan files, that conform to the FedRAMP requirements relating to continuous vulnerability scanning and monitoring.
The successful completion of the JAB review paves the way for 3PAO and the CSP to remediate any documentation and system issues as required, and ascertain to address the JAB review comments appropriately. JAB reviewers will then review and validate the remediation and mitigation efforts, allowing the CSP to receive a formal authorization and P-ATO decision by the CSO present in the FedRAMP PMO.



 BLUF - Bottom Line Up Front
BLUF - Bottom Line Up Front