 BLUF - Bottom Line Up Front
BLUF - Bottom Line Up Front
The CMMC requires most federal contractors to be certified against its protocol, with certain exceptions for COTS product manufacturers. Understanding whether items qualify as COTS is crucial, as is knowing the specific cybersecurity requirements applicable to your organization. Collaborate with legal and cybersecurity experts to navigate these obligations. Strategize compliance by differentiating systems that handle CUI and leveraging existing controls efficiently to meet federal mandates like CMMC, FISMA, and others.
The emerging Cybersecurity Maturity Model Certification (CMMC) will mandate nearly the entire federal government supply chain and over 300,000 contractors to get audited and certified against the CMMC protocol (COTS products CMMC audit). The caveat is that some organizations that build Commercial-Off-The-Shelf items or Commercially Available Off-The-Shelf (COTS) products for the Department of Defense (DoD) do NOT require a CMMC certificate.
However, the devil is in the details! In this article, we explore what DoD Commercial-Off-The-Shelf products are, how to properly identify COTS products, when your organization may require a certification while dealing with COTS products, and whether the CMMC COTS exception applies to your business line.
What are COTS products?
There are many definitions of COTS products in the market today. For the purpose of the CMMC certification preparation and audit, the two most important definitions come directly from the National Institute of Standards and Technology (NIST) and the DoD’s Defense Acquisition University (DAU). The CMMC audit process utilizes concepts and language from both NIST and the Defense Federal Acquisition Regulations. It is critical for organizations to understand both of these regulations and definitions for COTS, as your auditor may not be familiar with your business and how your business works with DoD COTS products.
The NIST definition* is very narrow. In general, the NIST definition applies to companies such as Microsoft or similar categories of hardware and software product vendors that sell computing devices.
“Software and hardware that already exists and is available from commercial sources. It is also referred to as off-the-shelf.”
“A software and/or hardware product that is commercially ready-made and available for sale, lease, or license to the general public.”
“Hardware and software IT products that are ready-made and available for purchase by the general public.”
*https://csrc.nist.gov/glossary/term/commercial_off_the_shelf
The Federal Acquisition Regulation (FAR)** offers a much broader range of possibilities on what is and could be considered COTS. Here the term COTS is formally defined as the following:
(1) Means any item of supply (including construction material) that is–
(i) A commercial item;
(ii) Sold in substantial quantities in the commercial marketplace; and
(iii) Offered to the Government, under a contract or subcontract at any tier, without modification, in the same form in which it is sold in the commercial marketplace; and
(2) Does not include bulk cargo, as defined in 46 U.S.C. 40102(4), such as agricultural products and petroleum products.
**Part 2 – Definitions of Words and Terms | Acquisition.GOV
Small Manufacturers: How to Determine if you have COTS products or not?
Determining whether you have COTS products from your customer’s perspective is a very complex and challenging task. To simplify, first you should determine if you are receiving any engineering designs or custom development requirements to enhance your COTS products. If the answer is yes, you can safely assume that you are exchanging Control Unclassified Information (CUI).
However, many small businesses today use available COTS items as a base or a component to build and improve their own products, which are sold to customers within the DoD and commercial entities. The specifics of such product creation and assembly, utilizing other COTS and their components, are usually overcomplicated by intermingling data ownership, know-how, and intellectual property rights.
Thus, the determination of COTS exceptions should generally be made by business leaders and guided by competent cyber and legal experts on a contract by contract basis. The FAR definition is riddled with scenarios and interpretations that should be considered carefully under the supervision of a competent legal team. If you need help in understanding whether the products that you sell to your Prime are considered Commercial Items (CI) or COTS CMMC compliance exceptions, please contact our legal team to help you through this strategic decision-making process.
The Ignyte team leverages artificial intelligence to quickly assess any cyber liabilities and requirements that exist within your contracts to help you understand exposures. As a result, it ultimately helps develop a common reusable security framework. Our Contract Manager uses assistive technologies to extrapolate cyber requirements for analysts around the world.
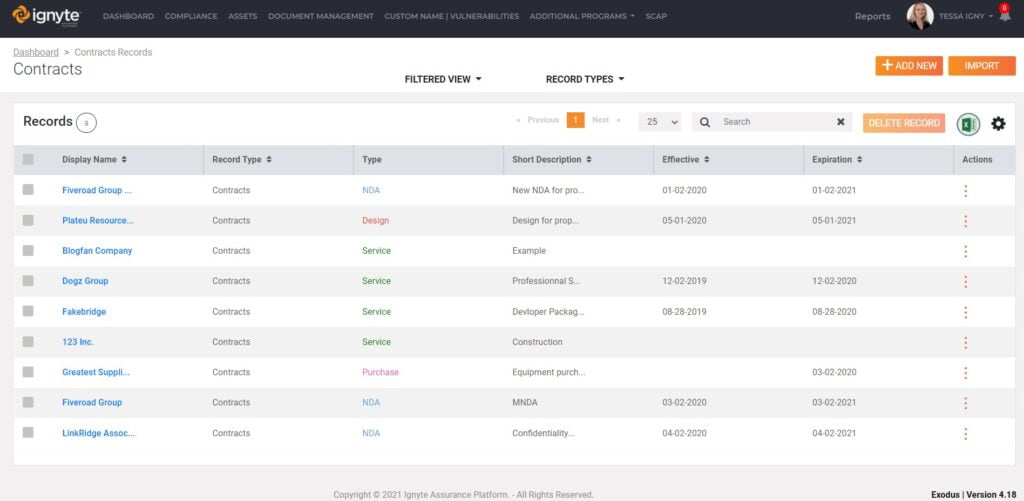
Do Software products require COTS products CMMC audit or similar processes to work with the DoD?
If you have complete ownership over the technical data rights for the product and have not developed the product using federal funds (e.g., Small Business Innovation Research (SBIR), Small Business Technology Transfer (STTR), Other Transfer Authority (OTAs), or other Federal Acquisition Authorities, etc.), then you can safely assume that you do not have to meet CMMC requirements. If that is the case, we would still encourage you to take this time to study your market and understand where your product is being utilized. Such analysis will help you to understand emerging requirements for proactive planning.
However, it is essential to carefully assess all the details that went into the research, design, and development processes of your software COTS products to determine if a CMMC exception is applicable. As mentioned previously, the devil is in the details. The Ignyte team recommends that you work closely with business, legal, and cyber experts to perform due diligence on whether your organization is obligated to meet the CMMC requirements. Their expertise will help your organization understand where and when to leverage CMMC requirements for the security of your COTS products. Failure to perform this critical step can lead to a loss of time and resources in properly scoping your organization’s environment.
The DoD and the federal government are currently placing various types of cybersecurity requirements in front of all procurement and acquisition activities, including software, firmware, services, unique processes, and small machine parts. The below chart was issued by the DAU as a quick reference guide and list “Cybersecurity” as the first item in the acquisition process before purchasing any product or service.
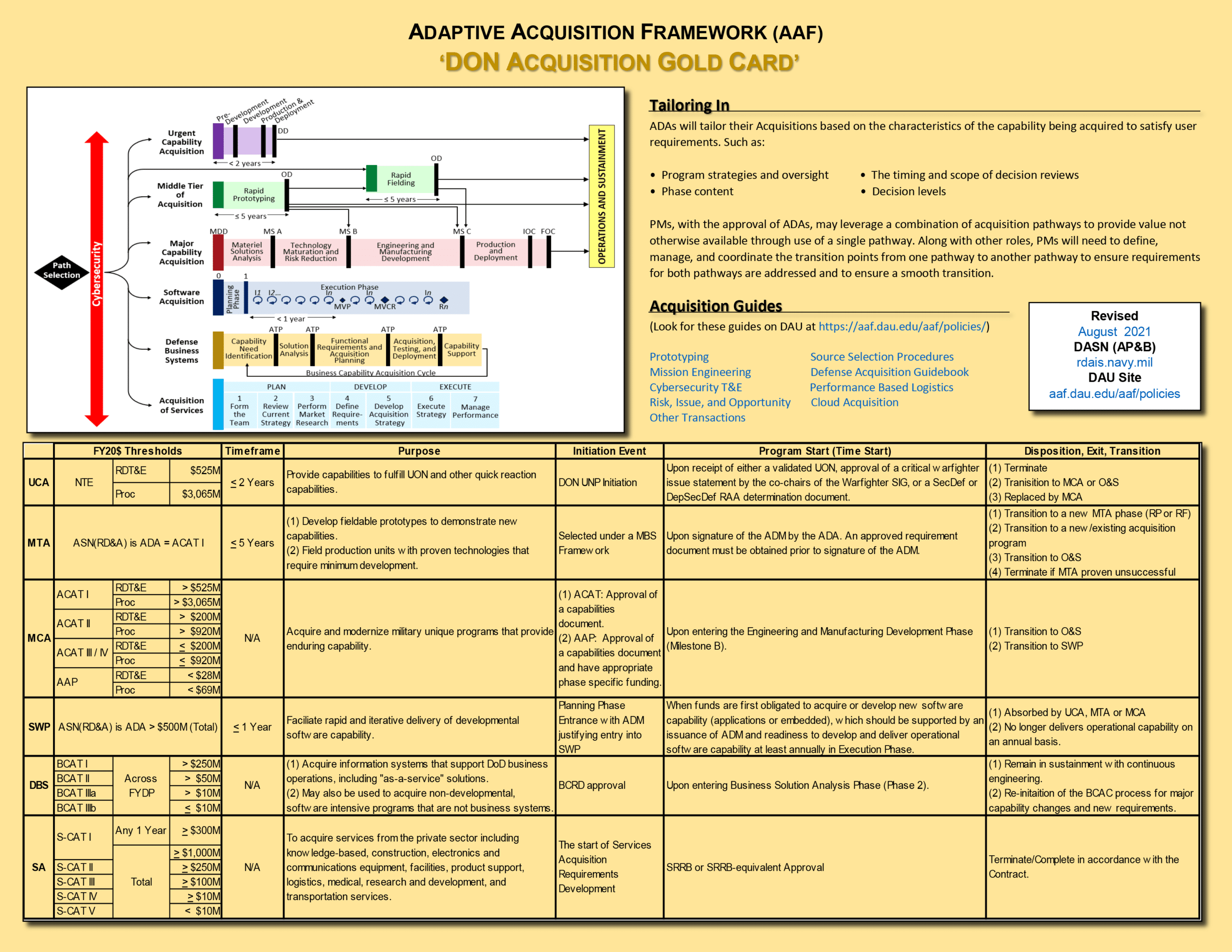
What other cybersecurity requirements can apply to your business as a COTS product manufacturer?
If you are doing business with the government, eventually, some form of cybersecurity requirement, or perhaps even CMMC flow-downs, will apply to your organization. So it’s only a matter of time; the trick is figuring out when you should start preparing for these requirements. Therefore, planning and strategy alignment with your business growth cycles are critical.
Like in the commercial sector, multiple requirements (e.g., HIPAA, PCI, SOx, etc.) are applied explicitly to each organization based on their vertical (i.e., Healthcare, Finance, Manufacturing, etc.). Cyber requirements in the Federal sector are generally based on the specific agency you are working with, what products or services you are selling to them, and the overarching Federal mandates applied to each agency. CMMC is a similar Federal mandate that is used within the DoD supply chain.
An essential regulatory requirement that you should know is FISMA – Federal Information Systems Management Act. FISMA applies to all federal systems, including products used by federal agencies. Many times, agencies leverage FISMA authority to flow down specific security requirements to individual small businesses. FISMA and CMMC both leverage various NIST cybersecurity specifications to comply with their regulatory requirements.
Ignyte leverages its mapping engine to rapidly conduct overlap analysis between any two or more cyber regulations to help analysts and business leaders quickly understand leverageable cyber controls that organizations may already have in place. This rapid upfront analysis enables you to save time and money when implementing CMMC and helps you get through the CMMC audit more efficiently.
For any prime contractor under regulatory pressure like CMMC, or other agencies looking to work with an agile organization, Ignyte can assist you with determining the complete scope of risk, governance, and compliance work that your organization needs to accomplish. In addition, Ignyte can help you accelerate, implement, and automate existing cyber requirements – such as FedRAMP, JSIG, DCSA’s RMF, DISA APL, FISMA, and many others.
Contracts that generally include cybersecurity requirements for COTS products or non-COTS services
As indicated in the graphic above, the federal government is mandating some security aspects in all of its procurement activities. There are hundreds of ways a prime or the U.S. Government can insert security flow down requirements into any contract or a federal business relationship. As a result, your organization should be performing contract inspections and have an understanding and awareness of all the potential CUI information you may have submitted in various government portals (e.g., System for Award Management (SAM), Supplier Performance Risk System (SPRS) portal, or SBIR submission portals, etc.).
There are many entries into the federal government, and at each entry point, you may have obligated yourself to implement cybersecurity controls within your organization. Below, we cover some common contractual obligations and methods of where you might see these requirements, and how they might look in sample clauses that the Ignyte contract analysis software finds.
- A contract that mentions the issuance of form DD-254. DD Form 254 is a U.S. publication referenced in the DFAR and applied to contracts involving access to classified information by U.S. contractors. If you have a DD-254 contract, you are well aware of the additional requirements imposed from facility clearances to maintain specific and advance security on information systems.
- A FISMA clause baked into your contract with language such as “At a minimum, systems, programs, and applications included in the products and services offered must comply with the documented security assessment and authorization (A&A) policies issued by the Office of Management and Budget (OMB), standards and guidance issued by the National Institute of Standards and Technology (NIST), and the Federal Information Security Modernization Act of 2014 (FISMA 2014) (44 U.S.C. 3551 et seq.)”.
- ITAR or EAR contract compliance requires you to implement security controls around the import of specified technologies and techniques to protect information leaving the United States.
In addition to the above requirements, a small business should inspect all of its terms and agreements related to a specific contract. Additional agreements and addendums – such as Non-Disclosure Agreements (NDAs), Quotes, Supplementary terms, and end-user license agreements (EULAs), etc., can contain security requirements. As part of your corporate risk management planning, these requirements need to be part of your CMMC strategy to get the most out of your security controls implementation.
COTS and CMMC Audit – Key Considerations
Most auditors are ill-equipped to fully understand the intricacies of determining how your business consumes or delivers COTS products to the federal government as a supplier in the complete supply chain. As mentioned earlier, determination requires help from legal and cyber professionals. The auditors’ perspective is concerned strictly with the identified scope to quickly and efficiently conduct their audit. We cover how to prepare for the audit here.
However, if your business has several commercially available products in large quantities, you may need to plan your audit specifically around areas that need proper coverage. Excluding areas of your business that have COTS can save you the time and resources required when going through the audit. Business systems used to primarily service and manage specific COTS products should be considered out of the inspection scope to reduce the impact of the audit. The following are some key areas to focus on during your audit process:
- Ensure a clear understanding of what is considered CUI according to your own data classification policy.
- Know the key business areas and supporting technology systems that maintain the majority of your CUI.
- Separate the majority of systems containing CUI versus focusing on ALL systems for the audit scope. Unless you are operating in a classified environment, all systems (especially laptops) eventually connect. However, it is critical to logically separate your environment into CUI and non-CUI areas to control the audit properly.
- Be realistic with your environment separation. We have seen many organizations purchase hardware to build an enclave that they never plan on using. This decision typically leads to failure and also to inefficient use of resources.
If your CMMC auditor is set on inspecting all areas of your organization without first understanding your core business and how COTS may impact the assessment, then having a call with the Ignyte legal team could help the auditor correctly understand the scope of your audit.
COTS Products and your CMMC – Strategy Considerations
For small businesses struggling with multiple requirements when assembling their COTS solutions to sell to the government, it is critical to start working from a contract perspective and capture the relevant information. You most likely have started doing some of this within your ERP systems to better understand your financial risk and the actual cost of building your product. Now, you need to capture this information within a legal and technology risk management platform to correctly estimate the risk associated with not implementing reasonable controls within your environment. Upon capturing this information, the Ignyte Platform automatically links it to existing technologies that hold and maintain your CUI and help secure those technologies with the Ignyte security operations suite.
Your CMMC strategy must show complete traceability from your business down to technologies in a business risk-oriented manner. Without this process, you could be left with implementing 30 to 50 technologies for CMMC that may not add value to your overall business and make your environment more complex and challenging to maintain.
Starting the entire CMMC conversation with your business growth in mind will help you sync the implementation of various tools and technologies within your organization.



 BLUF - Bottom Line Up Front
BLUF - Bottom Line Up Front